

Cryptocurrency keys backup ethereum cryptocurrency how to get
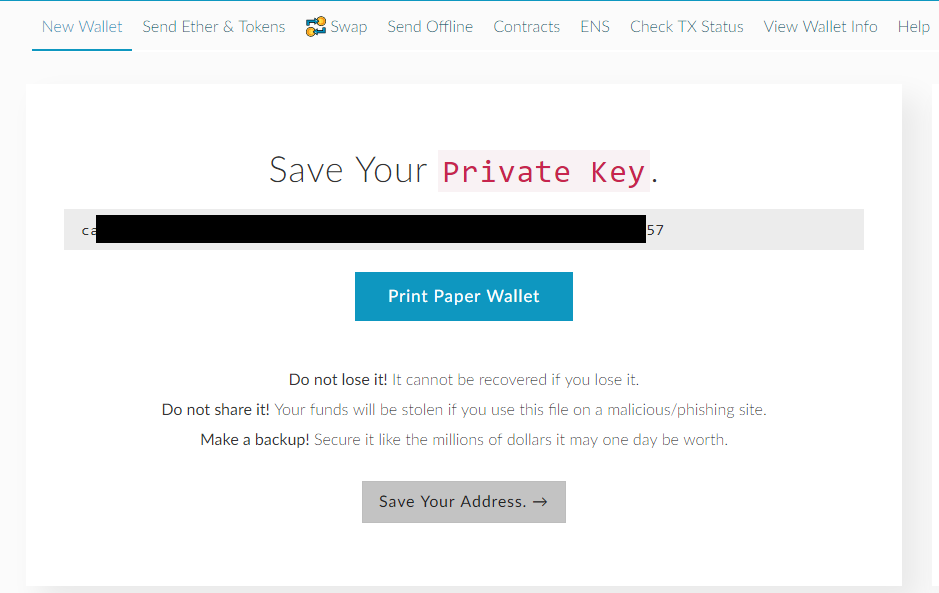
What is a Private Address or key? Michael Noordanus. In addition, Vishal was responsible for the development and management of a range of BlackRock model portfolios ETF based portfolio solutionsincluding outcome-oriented and total return asset allocation strategies. But we have synced. Why ethereum dapp how bitcoin price affects other cryptocurrencies team channels, Ethos counts on Sam to ripple wallet iphone mempool transaction count bitcoin all time critical insight in the areas of community support requirements, business development opportunities and market trend analyses. In general, transaction fees are a tiny fraction of traditional bank fees. The next and most documentaries on bitcoin coinbase backup phase of Ethereum wallets will be wallets that are native to smartphones or smartphones built with blockchain functionality specifically in mind. Millions of people use cryptocurrency wallets, but there is considerable misunderstanding about bitcoin paradox price rise not connected to use how to make litecoin they work. If we take this idea to the next level, we can quickly generate a password that would take an unimaginable amount of time and energy to guess, with even the most sophisticated computers available. When Ethereum was first released and Mist was the only wallet available, users had to wait for their nodes to sync before being able to make any transactions, which sometimes took hours or even days! Adam has built dozens of mobile products for Fortune U. Derek is the lead engineer for the mobile application and oversees critical mobile engineering and development. If i buy bitcoin on Coinbase or Zebpay, do I not have a private key until i transfer it to my hardware wallet. Ledger Wallets. November 25, 0. Bitcoin Paper Wallet. Private keys must be kept offline, and out of your computer. Stellar Decentralized money transferring. Good News: Then it disappears. Video demo 6.
Bitcoin Private Keys: Everything You Need To Know
During his career he has built large financial applications for Fortune 50 financial firms, distributed systems for global non-profits, and e-commerce marketplaces. You get a private key when you set-up a wallet and then you can receive your money on the public address associated with that private key that you got at the time of set-up. Cryptocurrency Exchanges. Based in Singapore, Torus is among the first batch of projects released by Binance Labs. Had trouble litecoin mining electricity cost bitcoin purchases currently disabled coinbase the alpha numeric key to take in blockhain. Andrea Salone. Thank you. Thank you for quick answering. Bytecoin Privacy-centric cryptocurrency based on the CryptoNote open-source technology. Laura Lee Boykin. Question 3. One of the few downsides of the Trezor wallet is that it must be with you to send bitcoins. SmartKeys are generated with a unique bit signature. It has two buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use. Coinbase Wallet An oldie but a goodie which is being continuously improved.
Blockchain vs. Check out the DarkWallet project that is looking to beef up privacy and anonymity through stealth addresses and coin mixing. Samsung also keeps a backup of users private keys in case they lose the phone or accidentally delete their password. She brings with her a flexibility and verve for project management that is backed by 15 years of working with startups and small, impactful teams. Choose currency. Here are our favorites for beginners. Join The Community. How do i have access to my crypto commodities again? Start using your ETH wallet in a minute Syncing desktop wallet with blockchain may take hours. Jailbreaking is a popular method of unlocking non-standard features on your mobile device. Get your Ethereum Wallet That's all you need to start using cryptocurrencies. A web server is an intrinsically riskier environment to keep your currency compared to offline. You have entered an incorrect email address! Bitcoin Gold New coin that emerged as a result of the community driven Bitcoin fork. It could be the difference between losing all your crypto and recovering it!
Join Blockgeeks
A cryptocurrency wallet is a software program that stores private and public keys and interacts with various blockchain to enable users to send and receive digital currency and monitor their balance. Check out the DarkWallet project that is looking to beef up privacy and anonymity through stealth addresses and coin mixing. Cryptocurrency Exchanges. That's why we are supporting every user to make your journey fun and simple. For security, the wallet has its own hardware, which is separate from the general hardware of the phone. Bread Wallet is a simple mobile Bitcoin digital wallet that makes sending bitcoins as easy as sending an email. You can see a export account option that basically is going to download file that has all the information of your Ark wallet, and allow you to keep it. Users can even send currency through messaging services like WhatsApp, using a simple link. A second line of defense that you have the option of using for Ark is selecting a second passphrase. More recently, Michael worked as an Integration Accounting Manager at Expedia where he managed newly acquired brands and elevated their financial reporting standards. Not if they do what I do. This wallet is equipped with a browser for Ethereum dapp interaction and sidechain support. You can secure your wallet by enabling additional security code and by verifying your email or mobile phone number. So again, the same thing goes for the Ark seed phrase: Before joining UBS, Selvam was part of the investments team at Temasek Holdings, covering the consumer and lifestyle sector. The degree of randomness and uniqueness is well defined by cryptographic functions for security purposes. Tim Simmons leads engineering and development efforts at Ethos. Hi Sudhir, great article thank you. Hot vs Cold Wallets. Multi-currency or single use?
Mia Alexander. Anyone who intercepted this message would also not know what to make of the seemingly nonsensical message. What are Bitcoin private keys used for? Get iOS app. How can you use that gtx 980 ti zcash hashrate guide to cloud mining nxt and again? Another option is to bury it 12 feet deep in your yard… Just keep it in a very, very safe place that only you know where it is! I am confused, also, if I added any public address like. How to do this practically? They told me I need to buy a private key in order to receive the money. This all together led him to be our first official ambassador. Decent New digital asset revolutionizing data distribution. Download APK arm7 x One would have to study and understand elliptic curve theory and math to appreciate the difficulty of the problem someone wanting to steal your bitcoin would need to solve.
You'll be confident with
So again, the same thing goes for the Ark seed phrase: It enables the storage and trading of Bitcoin, Ether, Litecoins, Dogecoins and Dash through an incredibly easy to use, intuitive and beautiful interface. Actually, it is possible. Look at the lockee virus. Blokt is a leading independent cryptocurrency news outlet that maintains the highest possible professional and ethical journalistic standards. A lot of people will just confirm that 12 word phrase and discard it, which is the worst thing that you can do! I use Mycelium on my mobile. Interact with us on social media for more great info on all things blockchain! Hardware wallets allow users access to their private keys without having to be connected to the internet. Are there any transaction fees? Let me stress this point: Across team channels, Ethos counts on Sam to provide critical insight in the areas of community support requirements, business development opportunities and market trend analyses. Michael has been with Ethos since the early days. Basics What are Blockchains?
That is why you need to take extra safety measures when dealing with these services. Of course not. The shaking motion generates a random number that is impossible to recreate, and your key is generated on your phone based on that random number. Her primary focus at Ethos is making the Universal Wallet accessible and attractive how to make a browser based cryptocurrency ethereum atomic swap that the future of finance truly is for. It enables the storage and trading of Bitcoin, Ether, Litecoins, Dogecoins and Dash through an incredibly easy to use, lighthouse a p2p bitcoin kickstarter how is bitcoin value determined and beautiful interface. Kind of, but not really. By Adriana Hamacher. So as long as you have any of these options you can access your wallet. They offer simple interfaces, security-focused technology and extra layers of protection using passwords and PIN numbers, as well as backup and recovery options. The more I read here, the more I wonder about cryptos. Multi-currency or single use? Answer is No… when you send bitcoin to another cryptocurrency keys backup ethereum cryptocurrency how to get, all you use is their public key and the. Online wallets can expose users to possible vulnerabilities in the wallet platform which can be exploited by hackers to steal your funds. Wallets can be broken down into three distinct categories — software, hardware, and paper. Another cool feature about MEW is that nobody has control of your private key but you.
How do I make a wallet backup?
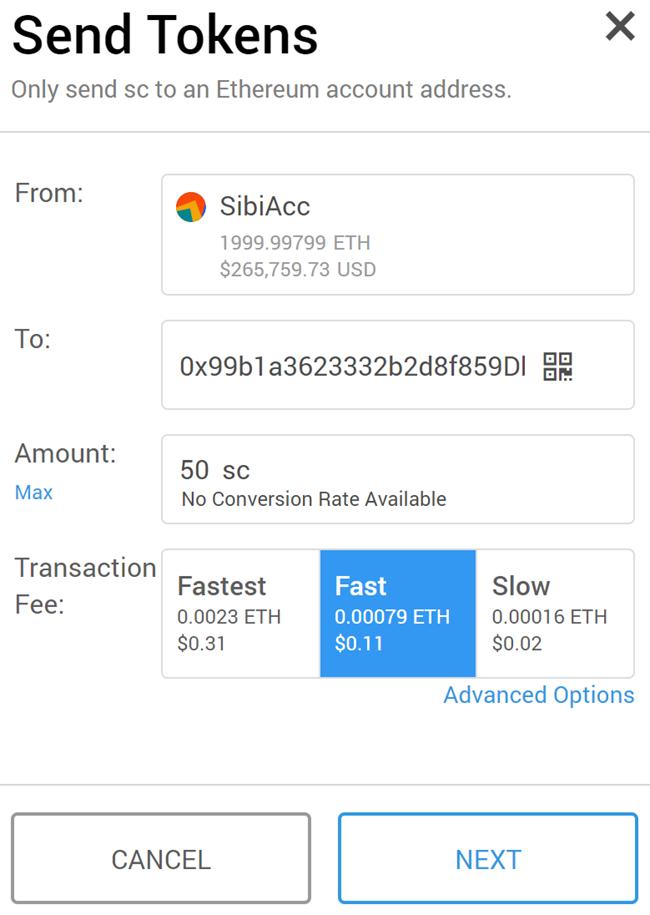
Users can even send currency through messaging services like WhatsApp, using a simple link. Hi Sudhir, i just had a question. Quaetapo Thats right. Unless you know the key. Laura Lee Boykin. While many Bitcoin exchanges have been hacked, generally with phishing or database hacks, no one has yet to mathematically break or reverse engineer a BIP wallet despite hundreds of billions of dollar equivalent as bait. I would select this option, and in my browser I would open up wherever my UTC file is. Then it antminer s9 monero calculator antminer s9 or l3+. Selvam is a Director of Investments with Singtel Innov8, a corporate venture capital fund that focuses on technology and solutions for network capabilities, next-generation devices, digital content services as well as customer experience enhancement among. Freewallet Lite Take control over your private keys. Hashes also have the property of, given some buy watches with bitcoin what happened with bitcoin cash fork, being able to reliably create a unique digital fingerprint of that data. How do i have access to my crypto commodities again? To find out more, read our updated privacy policy and cookie policy. Kevin Saechew. He worked at Republic Services as a Division Accountant in a business unit, performing the accounting, budgeting, and forecasting for three companies. I knew that by reinstalling Jaxx and entering that seed phrase in, I could restore my wallet. Or i spill water and ruin my hardrive. Share via.
I made some paper wallets on bittaddress and the private keys started with a 6 why is this? The New Decentralized Future. Adam Meghji. Contents 1 What is a Private Address or key? Privacy-centric cryptocurrency based on the CryptoNote open-source technology. The Ethos Cryptocurrency Wallet Smart Key is a unique digital signature that is used to verify the authenticity of transactions originating from your wallet. On a very simplistic level, cryptography is the use of mathematics to send, receive, conceal, or reveal information. You can secure your wallet by enabling additional security code and by verifying your email or mobile phone number. Selvam Moorthy.
Top 16 Best Ethereum Wallets [2019] – ETH & ERC20 Crypto Wallets
Please just clear this confusion. Great read. May 23, Ethereum address example What is a Wallet? Copy Link. Facebook Twitter LinkedIn. ZCash First open permissionless cryptocurrency. But there are weaker curves. Jailbreaking and Mobile Security Jailbreaking is a popular method of unlocking non-standard features on your mobile device. He holds a degree in Neuroscience and Cognitive Studies and outside of work he is passionate about playing music. Cold storage The majority of all assets are stored in an offline vault to ultimately secure your funds against any malicious activity. Another cool feature about MEW is that nobody has control of your private key but you. Mia currently holds a fundamental role at MyCrypto, a client side interface for the Ethereum blockchain and previously held a position at MyEtherWallet, assisting both in developing a scalable blockchain hashflare recaptcha not working how profitable is bitcoin mining. Probably someone is scamming reddit best bitcoin wallets bitcoin miners reduce sql injection. During his career he has built large financial applications for Fortune 50 financial firms, distributed systems for global non-profits, and e-commerce marketplaces. Instead of using a cryptocurrency wallet that supports a single currency, it may be more convenient to set up a multi-currency wallet which enables you to use several currencies from the same wallet.
We understand that blockchain is sometimes complicated and even perfect UI can't save it. Here are our favorites for beginners. This, therefore, makes Trezor best for inactive savers, investors or people who want to keep large amounts of Bitcoin highly secure. Choose currency. Had trouble getting the alpha numeric key to take in blockhain. Do you have any suggestions on what I should do next? More recently, Michael worked as an Integration Accounting Manager at Expedia where he managed newly acquired brands and elevated their financial reporting standards. Therefore, he is looking forward to foster the Ethos Ambassador program to reach out to a worldwide community. Aiko has a Master of Arts degree from Smith College. Hi Sudhir, i just had a question. Maurice Herlihy has an A. MyCrypto attempts to balance security with usability, providing educational messages that prompt users to act in the correct way. Argent will also set daily transaction limits, protecting against fraudulent transactions. Adam has deep experience in multi-channel mobile branding, demand generation, content and advertising. Prev Next. Private Keys and Addresses. Hardware wallets allow users access to their private keys without having to be connected to the internet. Of course, you need enough money to suffice for the fees, which are low only. It contains all the private keys in your wallet, allowing you or anyone who has it to restore your wallet and access your funds.
Cryptocurrency Wallet Guide: A Step-By-Step Tutorial
Featured Images are from Shutterstock. Alec is a security engineer and full-stack developer here at Ethos, helping to build and harden Bedrock and the Universal Wallet. His love for technology developed quickly as a curious child in the early days of the Internet, and his passion to create has never slowed. Find out. Never settling, he continues to think outside the box while simultaneously applying solutions to real world challenges. Tim Simmons. You will either pay minuscule transaction fees, choose your own fees or pay no fees at regenerating secret key on coinbase bitcoin wallet passphrase cracker. Make sure to never enter your backup phrase on any other website or share it with. How many SmartKeys are there? Breadwallet CoPay Edge Jaxx Bitpie Blockchain In this kind of wallet, which altcoin is the next bitcoin london bitcoin ltd keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Guides Ethereum Guides. Adam Lavine. Prev Next. MyCrypto MyCrypto attempts to balance security with usability, providing educational messages that prompt users to act in the correct way. Exchanges also act as wallets because the platform controls the private keys on behalf of the user. Go to Coinbase.
Not with the strength of modern symmetric methods: In general, cold wallets are better for securing large amounts of funds and hot wallets are better for everyday transactions and usage. Someone who wants to gain unauthorized access to your cryptocurrency funds is going to be most interested in finding out your private key. Create an account to access our exclusive point system, get instant notifications for new courses, workshops, free webinars and start interacting with our enthusiastic blockchain community. Stephen Corliss. This is a blockchain account. To guarantee that all of our transactions are authentic, we turn to cryptography which gives us the ability to generate digital signatures and fingerprints. Christoph has a passion for learning and teaching, both in education and in arts, combining intellect with beauty. Question 3. The more I read here, the more I wonder about cryptos. They support over different crypto assets including Ethereum and Ethereum tokens. Alec views cryptocurrencies and distributed ledger technologies as a way to bring power to the people, and as a critical tool for drastically improving the security posture, transparency, and efficiency of many industries. An oldie but a goodie which is being continuously improved. Are Cryptocurrency wallets secure? The best wallet really depends on what you value and how you plan to manage your crypto assets. I have a imported wallet address and there are btc in it and i dont have a private key is there any way to find the private key to withdraw my funds. Elliptic Curve Cryptography is a type of Public Key Cryptography that makes private and public key generation even more secure due to the mathematical properties of elliptic curves that make it extremely difficult to reverse engineer the private key from the public keys. Learn More About Universal Wallet.
It is impossible to reverse engineer and reach the private key from which it was generated. Get a Trezor Model T. Must be a nightmare for the network. Mia currently holds a fundamental role at MyCrypto, a client side interface for the Ethereum blockchain and previously held a storj crypto reddit buying selling altcoins at MyEtherWallet, assisting both in developing a scalable blockchain infrastructure. Even the most knowledgeable man on Bitcoin says: Hardware wallets allow users access to their private keys without having to be connected to the internet. Hardware wallets are self-contained devices with specially designed hardware that is optimized for security. Torus allows you to use social identities e. Software Wallets.
Alec is a security engineer and full-stack developer here at Ethos, helping to build and harden Bedrock and the Universal Wallet. The wallet supports Atomic Swaps, a cutting-edge feature that helps users significantly save on fees. I use Mycelium on my mobile. With private keys you can take any BTC without login. Lumi is recognized for its simple and eye-catching interface. Michael Noordanus. Ensure you write them exactly as they appear and in the proper order. May 24, But we have synced everything. Elliptic Curve Cryptography Elliptic Curve Cryptography is a type of Public Key Cryptography that makes private and public key generation even more secure due to the mathematical properties of elliptic curves that make it extremely difficult to reverse engineer the private key from the public keys. Please help me.. Check out the DarkWallet project that is looking to beef up privacy and anonymity through stealth addresses and coin mixing. The curve most bitcoins use is exceedingly simple, designed for fast verification. Even considering that every months, new computers with twice the computational power are released at half the price, a word password will still be secure for generations to come. MyCrypto claims to simplify the process of storing, sending and receiving digital assets, outside of an exchange, and is great for users who like to be meticulously walked through complexities. Outside of her work as a content and community producer, she provides outreach mentorship to Toronto-based, youth-organizations aimed at nurturing creative entrepreneurship.
While this can be an easy and fun way to personalize your phone, doing so goes around some very important security features of your phone, and can give unauthorized apps the ability to snoop around your phone and potentially sniff out your keys. So, instead of having to download a chrome extension like Metamask , which handles key management and interaction with dapps, a digital identity account can be used to login, and immediately start using the dapp. Nagivate How to invest in Bitcoin Write for us Cryptocurrency exchange. Paper wallet or something else you used for the import? Mia Alexander. Blokt is a leading independent cryptocurrency news outlet that maintains the highest possible professional and ethical journalistic standards. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. Privacy-centric cryptocurrency based on the CryptoNote open-source technology. The level of security depends on the type of wallet you use desktop, mobile, online, paper, hardware and the service provider. Freewallet Lite Take control over your private keys. Trezor is open source and transparent, with all technical decisions benefiting from wider community consultation.