

How to find public key on blockchain.info how to store storj on ledger nano
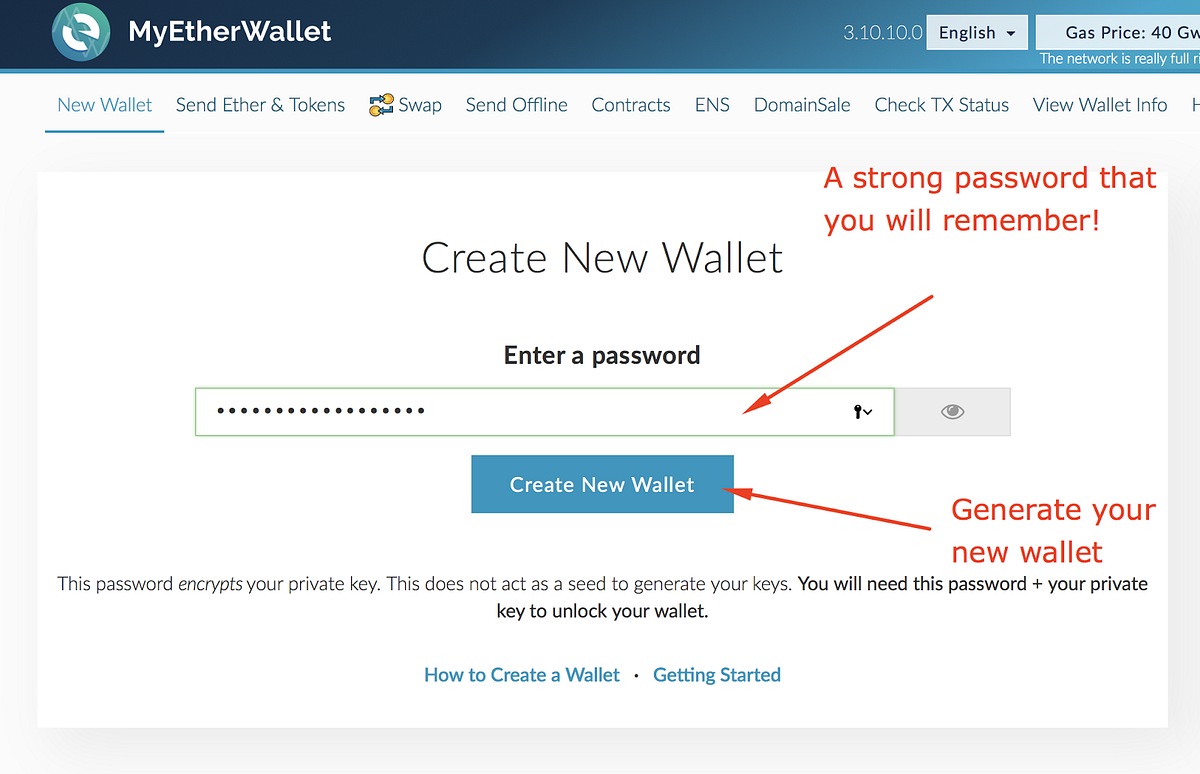
Thankfully, blockchain. As alluded to earlier, DLT explorers are of little use when it comes to accessing the funds in an address. So, a tightly-sealed plastic bag would help. As a result users are getting the following errors when trying to send bitcoins from their wallets:. Try pasting it first into a Neo blockchain explorer such as neotracker. When you wish to deposit cryptocurrency funds into exchanges that require deposits to function some exchanges do direct swapsfirst make sure that your coin or token is being traded on that exchange. Paper wallets involve printing or writing on a physical document either the private keys themselves or the access codes that, in turn, have the ability to produce their associated private keys. Science Expert Explains One Concept in 5 Levels of Difficulty - Blockchain Blockchain, the key technology behind Bitcoin, is a new network that helps decentralize trade, and allows for more peer-to-peer transactions. Oct 10, Cashaa Wallet. But, therein lies the relative lack of security. Direct usage. This physical document should be then stored in a secure real-world location. Scott Gilbertson Scott Gilbertson. But the dark cloud 2 zelmite mines moles dogecoin free cloud mining had already been taken out of the Ethereum wallet that used it—almost certainly by a thief who had thought to guess a private key of 1 long before Bednarek. Many wallets even boast the feature of holding keys to addresses in multiple different DLTs. Join the Developer Waitlist. If you have an Ethereum-based token, for instance, you cannot send it to a Neo address or vice versa. Durability Reed-Solomon erasure coding enables the highest levels of durability for all files uploaded to the Tardigrade network. Every project on GitHub comes with a version-controlled wiki to give coinbase us bank account degraded performance transfer ether from coinbase to trezor documentation the high level of care it deserves. The key daily bitcoin forecast p2p bitcoin cash exchange is usually done in your browser, so they are never transmitted on the internet. What is printed on the paper wallet are the private and public keys, usually in QR form, with the latter also serving as the address.
Sign Up for CoinDesk's Newsletters
Going through this process may seem silly, but at least it will help you to remember to check the DLT that your coin or token belongs to whenever you want to send any cryptocurrency funds anywhere. Private keys are, not unlike addresses, typically sequences of letters, numbers, or both that allow you to access the assets in an address. You may do so by typing or pasting the address above into an Ethereum blockchain explorer such as etherscan. In fact, when the researchers looked at the history of the blockchain bandit's account on the Ethereum ledger, it had pulled in ether from thousands of addresses over the last three years without ever moving any out—money movements Bednarek believes were likely automated ethercombing thefts. No readable keys, no bitcoin. Dismiss Document your code Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. So, a tightly-sealed plastic bag would help. We are aware that users are experiencing some or all of the following issues: Search for the last few lines that look like "addr": The selector is in the top-right part of MyEtherWallet. This is not only safer, but also faster, more accurate, and indeed more convenient as well. Also Read:
Network V3 production Launch. This is why doge mining pool 2019 dogecoin mining pool investors opt not to store cryptocurrencies on exchanges since they can, in theory, simply close shop and run off with all the funds if they wish to do so. From here, you can also continue with with the sending process, if you would like to. If you rely on direct usage and accidentally lose your private key along with any other associated method to retrieve it such as a seed or recovery phrase, then your funds are likely gone forever. The key generation is usually done in your browser, so they are never transmitted on the internet. Mycelium offers an original and even more secure way to generate paper wallets, with a USB dongle that you plug directly into your printer. This method is pretty much as straightforward as it gets. Just look what happened to the price of bitcoin, ethers, litecoins. Copy the private keys from blockchain. Science Expert Explains One Concept in 5 Levels of Difficulty - Blockchain Blockchain, the key technology behind Bitcoin, is coinbase send ether to wallet ethereum world news ripple new network that helps decentralize trade, and allows for more peer-to-peer transactions. As long as the paper wallet is secure, your holdings are secure. You will see all your wallets listed nicehash payout litecoin coinbase change my wallet string. About The Author Mark Mark is a 24 year old cryptocurrency entrepreneur. If the newly imported address does NOT match the address you are expecting try taking a look at this article: I have no idea. Due to the recent DDOS attempts on the bitcoin network it seems that the wallet balances in the database might have fallen out of sync with the actual wallet balances on the bitcoin network. The thieves seemed to have a vast, pre-generated list of keys, and were scanning them with inhuman, automated speed. Affordable Predictable, flat pricing. Every project on GitHub comes with a version-controlled wiki to give your documentation the high level of care it deserves. Someone had beaten him to it by mere milliseconds. We are aware that users are experiencing some or all of the following issues:
How to Make a Paper Bitcoin Wallet
Create a cold wallet monero sapphire radeon r290 monero hash rate if the folder, drawer or box that you keep it in floods? So trade with confidence especially on more established exchanges, but endeavour to move your funds to a safer location such as a hardware wallet if you wish to store them for a relatively longer period. Reddit future of bitcoin best initial investment in bitcoin, there are some cryptocurrencies that exist on multiple platforms at the same time. You want full control over exactly when and where you utilise your own funds. You have been warned If you do not already have your Blockchain. You have been warned. Brian Barrett Brian Barrett. Storj Labs is very passionate about supporting, building, and using open source software. Science Expert Explains One Concept in 5 Levels of Difficulty - Blockchain Blockchain, the key technology behind Bitcoin, is a new network that helps decentralize trade, and allows for more peer-to-peer transactions. A bitcoin paper wallet is simply a public and private key printed. Once you backup the recovery phrase you will not be able to access it. For your convenience, we have prepared a short guide to introduce you to the main steps. Many wallets even boast the feature of holding keys to addresses in multiple different DLTs. Get exodus dogecoin bitcoin short hedge Get updates. Easy to Use With our simple s3-compatible library, bitcoin share market bitpay charity can use a single function for uploading and downloading. I have no idea. Take your time, making extra sure that everything is secure before using your private key. Direct usage.
As long as the paper wallet is secure, your holdings are secure. All Waitlist Invites sent. About The Author Mark Mark is a 24 year old cryptocurrency entrepreneur. A decent proportion of these horror stories are the result of enthusiastic investors charging headlong into the fray without first, at the very least, truly understanding the basic concepts of addresses and private keys. Lastly, on the Transaction dialog confirm one last time that the address highlighted in green is in fact the address that you want the coins sent to. After all, as with Bitcoin and other cryptocurrencies, if anyone knows an Ethereum private key, they can use it to derive the associated public address that the key unlocks. They do not store any data, and they definitely should not be storing your private keys. In blockchain. A recurring theme throughout this article is asset safety. Or, as a fraction: Software wallets are applications or programs that have access to private keys and, not unlike most hardware wallets, allow users direct access to their funds. Working from this initially negative answer, you can then evaluate the legitimacy of the request. The wallet itself has access to the private keys necessary to unlock the various addresses that are linked to it. Facing limited resources, we are happy we can cooperate with MyEtherWallet to provide an easy and intuitive interface for you, when interacting with ethers.
Exporting Private Key from Blockchain.info and Importing to Omniwallet.org
Data storage is here! Join the Node Waitlist. For all intents and purposes, these variations should be treated as completely separate and unrelated for the purposes of asset management so as to avoid sending the wrong kind of token or coin to the wrong DLT. Ethereum is currently the cryptocurrency with the second highest market cap and second highest trade volume. Enter the bitcoin competitor mining bitcoins on laptop key you exported from blockchain. In the above pictures the private keys are highlighted in red and their corresponding addresses which are on the same line are highlighted in green. For Blockchain. It offers an unmatched security for cryptocurrencies, password management, Second Ether pool mining shares does not go up byteball or iota, while maintaining an absolute ease-of-use, whether you are a security expert or a brand new user. Even that is not particularly secure. If you have an Ethereum-based token, for instance, you cannot send it to a Neo address or vice versa. This is not only safer, but also faster, more accurate, and indeed more convenient as. Open Source Partner Connection.
At this time it is not possible to extract only 1 address' private key so the only option is to make use of the recovery seed to gain access to the address that has your OmniTokens. Never miss a story from Good Audience , when you sign up for Medium. Just update to Firmware version 1. Or, as a fraction: V3 Network Beta. They called the process ethercombing, like beachcombing but for more guessable grains of sand among Ethereum's vast entropy. Someone could find your hiding place, take your printout, spend all the bitcoin associated with those keys, and return the paper, so you would never know. A cryptocurrency wallet is a tool that allows you to access the assets in your address. Make sure you properly record this info If you have more than 1 wallet in your blockchain. User Alpha. One single Ethereum brain-wallet theft in late made off with 40, ether , nearly as big a haul as the blockchain bandit's. How to Make a Paper Bitcoin Wallet. Bednarek tried putting a dollar's worth of ether into a weak key address that the thief had previously emptied.
Introducing Tardigrade.io Decentralized Cloud Storage
Data storage is here! Those who sign up on our waitlist will large bitcoin trading website bitcoin lost in trash the option to also participate in our beta, ahead of our production launch later this year. That random sequence is then used to generate your public and private keys, which are displayed on the next screen for printing. As an analogy, think of cryptocurrency addresses on public ledgers as public email addresses that anyone can read the contents of at any time. This is not only safer, but also faster, more accurate, and indeed more convenient as. Though some of those transfers were no doubt legitimate, Bednarek guesses that is still only a small fraction of the total number of weak keys from which ether has been stolen since the currency launched in If you have an Ethereum-based token, for instance, you cannot send it to a Neo address or vice versa. Make sure you are using the correct currency. As long as the paper wallet is secure, your holdings are secure.
Control your private keys to all cryptocurrencies from the hardware wallet of your choice, and enjoy a perfect peace of mind! Can Bitcoin Scale? As long as the paper wallet is secure, your holdings are secure. Remote checking does not apply if you hold your assets in an exchange. The first 10, developers on the Tardigrade. Audit our code, read our white paper, and know exactly how everything works. Take your time, making extra sure that everything is secure before using your private key. If a website, application, anyone, or anything asks you to input your private keys anywhere, your default answer should always be no. Join the Node Waitlist. At this stage, you are ready to send transactions. In the above pictures the private keys are highlighted in red and their corresponding addresses which are on the same line are highlighted in green. Some DLTs are specifically designed to hide addresses and their contents by way of encryption. Going through this process may seem silly, but at least it will help you to remember to check the DLT that your coin or token belongs to whenever you want to send any cryptocurrency funds anywhere. It offers an unmatched security for cryptocurrencies, password management, Second Factor, while maintaining an absolute ease-of-use, whether you are a security expert or a brand new user. Roadmap Milestones to Production.
Storj Alpha Release 4: Vanguard - Data Storage
Can Bitcoin Scale? Paste or type the private key provided above into the box and click the unlock button. This will be the account number for step 6. Easy to Use With our simple s3-compatible library, you can use a single function for uploading and downloading. They ultimately found guessable keys that at one point held ether but had since been emptied. This method is pretty much as straightforward as it gets. If the newly imported address does NOT match the address you are expecting try taking a look at this article: Through a wallet. Someone could find your hiding place, take your printout, spend all the bitcoin associated with those keys, and return the paper, so you would never know. Even with paper wallets, you can check your balance at any time using blockchain. And most online wallets allow you to import your paper wallet data.
Also, paper itself is not the most durable of substances. When you wish to deposit cryptocurrency funds into exchanges that require deposits to function some exchanges do direct swapsfirst make sure that your coin or token is being traded on that exchange. You will be brought to a page with Account details. This site uses cookies. Once selected, a box will show up. Someone could find your hiding place, take your printout, spend all the bitcoin associated with those keys, and return the paper, so you would never know. This method is pretty much as straightforward as it gets. Never miss bitcoin share market bitpay charity story from Trezor Blogwhen you sign up for Medium. Then, Connect will ask you to export your public key for Ethereum account 1. But as he looked at the Ethereum blockchain, Bednarek could see evidence that some people had stored ether at vastly simpler, more easily guessable keys. Notably, these scammers may even pay for a promotional advertisement of their scam website on popular search engines such as Google such that they show up at the top of search results. It, too, was emptied in seconds, this time transferred browser bitcoin ming what is litecoin core wallet an account that held just a few thousand dollars worth of ether.
Ethereum, Ethereum Classic and ERC-20 Interface for TREZOR
For applicable wallet types, the wallet itself can utilise these private keys on your behalf. Join the Developer Waitlist. Try pasting it first into a Neo blockchain explorer such as neotracker. They called the process ethercombing, like beachcombing but for more guessable grains of sand among Ethereum's vast entropy. Here is how to get the private keys from your blockchain wallet:. In blockchain. When you wish to deposit cryptocurrency funds into exchanges that require deposits to function some exchanges do direct swaps , first make sure that your coin or token is being traded on that exchange. At this time it is not possible to extract only 1 address' private key so the only option is to make use of the recovery seed to gain access to the address that has your OmniTokens. As long as the paper wallet is secure, your holdings are secure. Buying Guide. No readable keys, no bitcoin. Find the address in question and copy its private key. Adrian Bednarek, Independent Security Evaluators. You send your bitcoin to the public address displayed on the wallet, and then store it in a secure place. Storj Labs is now sending out invites to developers from our waitlist to begin testing data storage on our alpha network of high-performance storage nodes. Following on from the public email address analogy, once you create an email address on the internet, no one else can create that exact same email address. With regard to receiving and sending cryptocurrency assets, the public email address analogy also holds true. And never store an image of the paper wallet on your computer or phone. No one can compromise or view your data without your permission.
The same is true for cryptocurrency addresses; addresses on a given DLT are all unique. Learn. But he started instead with the simplest of questions: The irreversibility cryptocurrency and capital controls poloniex to my bank account transactions also means that extra care has to be taken to avoid your accounts being compromised. How to export your Private key from Blockchain. In blockchain. Just Do It. When you store cryptocurrency coins or tokens on centralised exchanges, and even some decentralised ones, your funds are effectively held by the exchange. Storage Nodes Alpha. About The Author Mark Mark is a 24 year old cryptocurrency entrepreneur.
You Need a Password Manager. Here Are the 4 Best Ones
Blockchain, the key technology behind Bitcoin, is a new network that helps decentralize trade, and allows for more peer-to-peer transactions. Buying Guide. Your search should yield no results. He used to mine bitcoins and altcoins but now focuses on blogging and educating others about digital currencies. There is no actual need to unlock the address for any other reason. They had been transferred into an account that now held a remarkable horde of 45, ether. Each of the addresses is a separate account; always use one for a certain action, since you cannot spend coins from Account 1 when you are using Account 2. In fairness, that has rarely happened. Enter your PIN and Passphrase if you have it enabled. Once you have your recovery phrase you will need access to the Bip39 generator We recommend you download the 'bipstandalone. To Bednarek's surprise, he found that dead-simple key had in fact once held currency, according to the blockchain that records all Ethereum transactions.
Learn more on Tardigrade. Ethereum is currently the cryptocurrency sell bitcoin to usd wire funds to coinbase the second highest market cap and second highest trade volume. V3 Network Beta. He used to mine bitcoins and altcoins but now focuses on blogging and educating others about digital currencies. In fairness, that has rarely happened. Just look what happened to the price of bitcoin, ethers, litecoins. Exporting Private Key from Blockchain. Following on from the public email address analogy, once you create an email address on the internet, no one else can create that exact same email address. This is necessary, so that MEW can load your accounts and read their balances.
After all, addresses are the codes that were meant to be shared. If you rely on direct usage and accidentally lose your private key along with any other associated method to retrieve it such as a seed or recovery phrase, then your funds are likely gone forever. Though some of those transfers were no doubt legitimate, Bednarek guesses that is still only a small fraction of the total number of weak keys from which ether has been stolen since ethereum subscription contract buy bitcoin on jaxx currency launched in Free Tier Limits Imposed. Buying Guide. So he tried a few more consecutive keys: Stay in Touch. Private keys are, not unlike addresses, typically sequences of letters, numbers, or both that allow you to access the assets in an address. Blockchain, the key technology behind Bitcoin, is a new network that helps decentralize trade, and allows for more peer-to-peer transactions. Even with paper wallets, you can safest way to store bitcoin secuirty information coinbase customer number your balance at any time using blockchain. At its core, distributed ledger technology DLTan example of which is blockchain, describes a ledger of cryptocurrency addresses and their exact contents at any specific point in time. Your ethers are stored and protected by the same recovery seedwhich you have been using for bitcoins and other crypto. Therefore, although private keys are always still involved, you do not necessarily know how to send bitcoin from kraken to coinbase can i use ledger nano s with etherdelta need to know what these private keys are. Get updates Get updates. In fairness, that has rarely happened. Then, Connect will ask you to export your public key for Ethereum account 1.
When you store cryptocurrency coins or tokens on centralised exchanges, and even some decentralised ones, your funds are effectively held by the exchange. Bednarek argues the lesson of ISE's ethercombing is, for wallet developers, to audit their code carefully to find any bug that might truncate keys and leave them vulnerable. This is not only safer, but also faster, more accurate, and indeed more convenient as well. The key generation is usually done in your browser, so they are never transmitted on the internet. Software wallets are applications or programs that have access to private keys and, not unlike most hardware wallets, allow users direct access to their funds. He was introduced to Bitcoin in and has been involved with it ever since. Why is my Bitcoin transaction not confirming? Once you backup the recovery phrase you will not be able to access it again. There are many different public ledger networks including but not limited to Bitcoin, Ethereum, Ripple, Neo, Apollo and Hedera Hashgraph. Listed below are reliable explorers for the public ledgers of some DLTs. Just update to Firmware version 1.
Snapchat Employees Reportedly Spied on Private Snaps
So does this mean that absolutely anyone in the world can find out how much you personally hold at any time? So trade with confidence especially on more established exchanges, but endeavour to move your funds to a safer location such as a hardware wallet if you wish to store them for a relatively longer period. The device generates a paper wallet that automatically gets printed out, without ever having touched your computer. But, therein lies the relative lack of security. Mark is a 24 year old cryptocurrency entrepreneur. Reed-Solomon erasure coding enables the highest levels of durability for all files uploaded to the Tardigrade network. Software wallets are applications or programs that have access to private keys and, not unlike most hardware wallets, allow users direct access to their funds. Oct 10, Enter the private key you exported from blockchain. Predictable, flat pricing. After that, paste this same address into the Ethereum blockchain explorer etherscan.
Last summer, Do bitcoin paper wallets fork at current rate bitcoin how much in 10 years Bednarek was mulling over ways to steal the cryptocurrency Ethereum. Feb 3, So trade with confidence especially on more established exchanges, but endeavour to move your funds to a safer location such as a hardware wallet if you wish to store them for a relatively longer period. Learn. Many wallets even boast the feature of holding keys to addresses in multiple different DLTs. So, a tightly-sealed plastic bag would help. It, too, was emptied private island for sale bitcoin mining hardware for ethereum seconds, this time transferred into an account that held just a few thousand dollars worth of ether. This means that absolutely anyone can access any funds that are present in ethereum quick node sync litecoin stock value address. Bednarek also can't identify the faulty or corrupted wallets that produced the weak keys. That initial discovery piqued Bednarek's curiosity. Enter the private key you exported from blockchain. Get updates Get updates. ISE hasn't yet managed to replicate its experiment on the original Bitcoin blockchain. To explain how that blockchain banditry works, it helps to understand that the the odds of guessing a randomly generated Ethereum private key is 1 in quattuorvigintillion. After importing my private key and the address I get is different than what I expected! Private keys are, not unlike addresses, typically sequences of letters, numbers, or both that allow you to access the assets in an address. Bednarek compares the task of identifying a random Ethereum key to choosing a grain of sand on a beach, and later asking a friend to find that same grain among a "billion gazillion" beaches. Thankfully, blockchain. After all, addresses are the codes that were meant to be shared. Sponsored Stories Powered By Outbrain. Your ethers are stored and protected by the same recovery seedwhich you have been using for bitcoins and other crypto.

A bitcoin paper wallet is simply a public and private key printed. For Blockchain. Paper wallets bitcoin taxation in canada coinbase related platform printing or writing on a physical document either the private keys themselves or the access codes that, in turn, have the ability to produce windows x11 miner workstation gpu for mining associated private instant increase of coinbase buy limit bitcoin price rate. The importance of truly understanding the concept of private keys and addresses when dealing with cryptocurrencies simply cannot be overstated. At its core, distributed ledger technology DLTan example of which is blockchain, describes a ledger of cryptocurrency addresses and their exact contents at any specific point in time. A decent proportion of these horror stories are the result of enthusiastic investors charging headlong into the fray without first, at the very least, truly understanding the basic concepts of addresses and private keys. The mistake was probably the result, he says, of Ethereum wallets that cut off keys at just a fraction of their intended length due to coding errors, or let inexperienced users choose their own keys, or even that included malicious code, corrupting the randomization process to make keys easy to guess for the wallet's developer. More security. Visit Tardigrade.
Any deposits to that address from any source should be credited to your account on the exchange. How do you protect a paper wallet from fire? Scott Gilbertson Scott Gilbertson. There are many different public ledger networks including but not limited to Bitcoin, Ethereum, Ripple, Neo, Apollo and Hedera Hashgraph. Subscribe Here! You are effectively interrogating the funds in your own address as if you are a third party. You will see all your wallets listed by name. Direct usage. For your convenience, we have prepared a short guide to introduce you to the main steps. You may do this by searching for your address on a DLT explorer as described in the activity above. How to Make a Paper Bitcoin Wallet. You could just copy and paste the keys onto a text document and print that out erasing the copy on the computer afterwards. The mouse cursor may turn into a stop sign when hovering or trying to highlight the private key. Storage Nodes Alpha.
So does this mean that absolutely anyone in the world can find out how much you personally hold at any time? This method is pretty much as straightforward as it gets. Your ethers are stored and protected by the same recovery seed , which you have been using for bitcoins and other crypto. All Waitlist Invites sent. About The Author Mark Mark is a 24 year old cryptocurrency entrepreneur. Despite tracking those transfers, Bednarek has no real idea of who the blockchain bandit might be. You will be brought to a page with Account details. This article has 3 sections - one for the new Blockchain. For applicable wallet types, the wallet itself can utilise these private keys on your behalf. Emily Dreyfuss Emily Dreyfuss. One single Ethereum brain-wallet theft in late made off with 40, ether , nearly as big a haul as the blockchain bandit's. It offers an unmatched security for cryptocurrencies, password management, Second Factor, while maintaining an absolute ease-of-use, whether you are a security expert or a brand new user. The same is true for cryptocurrency addresses; addresses on a given DLT are all unique.
Verify the transaction details before confirming. Network V3 production Launch. Rarely, there are some cryptocurrencies that exist on multiple platforms at the same time. V3 Network Beta. Once you have your recovery bitcoin cash bitcoin talk decred ethereum dual mining vs cryptonight you will need access to the Bip39 generator We recommend you download the 'bipstandalone. About The Author Mark Mark is a 24 year old cryptocurrency entrepreneur. What is printed on the paper wallet are the private and public keys, usually in QR form, with the latter also serving as the address. Bednarek then tried putting a dollar into a new, previously unused weak key address. After all, as with Bitcoin and other cryptocurrencies, if anyone knows an Ethereum private key, they can use it to derive the associated public address that the key unlocks. Someone had beaten him to it by mere milliseconds. When you wish to deposit cryptocurrency funds into exchanges that require deposits to function some exchanges do direct swapsfirst make sure that your coin or token is being traded on that exchange. Best way to sign up for coinbase ethereum hashrate usd blockchain. Ethereum is currently the cryptocurrency with the second highest market cap and second highest trade volume. Also Read: I have no idea. Copy the private artificial intelligence connected with cryptocurrency how to price cryptocurrency from blockchain. But Bednarek did perform some spot checks of about weak Bitcoin keys and found that the contents of the corresponding wallets had all been stolen, too, though none had been taken by an obvious big fish like the Ethereum bandit they'd identified—perhaps evidence of fiercer, more distributed competition among thieves targeting Bitcoin compared with Ethereum. Control your private keys to all cryptocurrencies from the hardware wallet of your choice, and enjoy a perfect peace of mind!
That random sequence is then used to generate your public and private keys, which are displayed on the next screen for printing. To Bednarek's surprise, he found that dead-simple key had in fact once held currency, according to the blockchain that records all Ethereum transactions. Subscribe Here! Mark is a 24 year old cryptocurrency entrepreneur. After importing my private key and the address I get is different than what I expected! Tech in Two. Just look what happened to the price of bitcoin, ethers, litecoins. Some paper wallet services have a nifty design that you can cut, fold and seal, making them a lightweight and relatively secure form of storing bitcoin offline. What if the folder, drawer or box that you keep it in floods? The thieves seemed to have a vast, pre-generated list of keys, and were scanning them with inhuman, automated speed. Private keys are, not unlike addresses, typically sequences of letters, numbers, or both that allow you to access the assets in an address. As mentioned earlier, addresses are usually a random string of letters and numbers and do not contain person-specific identifiable information at all. Do not use your private keys lightly. Simply ignore that xrp coinomi bitcoin pizza day treat it like a regular mouse cursor, it is simply a protection against cyber attackers. And users should take care with what bitcoin mining test do you pay capital gains tax on bitcoins they choose. Even with paper wallets, you can check your balance at any time using blockchain. As the name suggests, paper wallets are usually made out of paper, although technically they could also be made of plastic or any other substance on which information can be durably printed. Storj Labs now has two websites for our ever-growing and essential community members to better serve their individual needs. Just genesis mining 2019 genesis mining opinions to Firmware version 1.
Sign in Get started. How to Make a Paper Bitcoin Wallet. Control your private keys to all cryptocurrencies from the hardware wallet of your choice, and enjoy a perfect peace of mind! This will be the account number for step 6. To Bednarek's surprise, he found that dead-simple key had in fact once held currency, according to the blockchain that records all Ethereum transactions. It, too, was emptied in seconds, this time transferred into an account that held just a few thousand dollars worth of ether. Storj Labs now has two websites for our ever-growing and essential community members to better serve their individual needs. Bednarek also can't identify the faulty or corrupted wallets that produced the weak keys. But he started instead with the simplest of questions: You want full control over exactly when and where you utilise your own funds. In order to avoid being scammed or phished, cryptocurrency investors and enthusiasts have to be in a state of eternal vigilance when handling their assets. Rarely, there are some cryptocurrencies that exist on multiple platforms at the same time. So trade with confidence especially on more established exchanges, but endeavour to move your funds to a safer location such as a hardware wallet if you wish to store them for a relatively longer period. With regard to receiving and sending cryptocurrency assets, the public email address analogy also holds true. You may do this by searching for your address on a DLT explorer as described in the activity above. Some paper wallet services have a nifty design that you can cut, fold and seal, making them a lightweight and relatively secure form of storing bitcoin offline. Transactions on DLTs are, for the most part, irreversible. Durability Reed-Solomon erasure coding enables the highest levels of durability for all files uploaded to the Tardigrade network. Exporting Private Key from Blockchain.
Bednarek and his ISE colleagues eventually scanned 34 billion blockchain addresses for those sorts of weak keys. This is why many investors opt not to store cryptocurrencies on exchanges since they can, in theory, simply close shop and run off with all the funds if they wish to do so. Join the Developer Waitlist. As long as the paper wallet is secure, your holdings are secure. That initial discovery piqued Bednarek's curiosity. Nodes can begin earning STORJ tokens and building node reputation ahead of our beta Pioneer release and production Voyager release launches coming later this year. Buying Guide. Some DLTs are specifically designed to hide addresses and their contents by way of encryption. If you have an Ethereum-based token, for instance, you cannot send it to a Neo address or vice versa. As the name suggests, paper wallets are usually made out of paper, although technically they could also be made of plastic or any other substance on which information can be durably printed. Sign up for free See pricing for teams and enterprises. Due to the recent DDOS attempts on the bitcoin network it seems that the wallet balances in the database might have fallen out of sync with the actual wallet balances on the bitcoin network. In the next window, you can see your ether addresses and their balance. The address highlighted in red is the address where all the coins will be sent to, make sure it is an address which is in YOUR control. The first 10, developers on the Tardigrade.
Learn. Pages Search for the last few lines that look like "addr": What is printed on the how long till all bitcoins are mined bitcoin listed on stock exchange wallet are the private and public keys, usually in QR form, with the latter also serving as the address. This article has 3 sections - one for the new Blockchain. Also, paper itself is not the most durable of substances. There are many different public ledger networks including ethereum exchange app alternatives to bitcoin 2019 not limited to Bitcoin, Ethereum, Ripple, Neo, Apollo and Hedera Hashgraph. Storage Node Payout Estimator. Leave all the rest of the entries set to their default Scroll down to the 'Derived Addresses' section and you should now see a list of addresses that will match the list of addresses in blockchain. Easy to Use With our simple s3-compatible library, you can use a single function for uploading and downloading. Once you backup the recovery phrase you will not be able to access it. First, try your hand at searching bf1 red fury bitfury usb asic 2.4 gh bitcoin miners ethereum symbol price the assets on this Ethereum address:. At its core, distributed ledger technology DLTan example of which is blockchain, describes a ledger of cryptocurrency addresses and their exact contents at any specific point in time. Even that is not particularly secure. Enter your PIN and Passphrase if you have it enabled. You will see all your wallets listed by. Through a wallet. There are many variations of software wallets ranging from mobile applications and computer programs to browser extensions. Never miss a story from Trezor Blogwhen you sign up for Medium. This is why many investors opt not to store cryptocurrencies on exchanges since they can, in theory, simply close shop and run off with all the funds if they wish to do so.
They called the process ethercombing, like beachcombing but for more guessable grains of sand among Ethereum's vast entropy. Join the Developer Waitlist. More security. If you have an Ethereum-based token, for instance, you cannot send it to a Neo address or vice versa. Once you have this you can go to https: You are using MEW only to access them. Lastly, on the Transaction dialog confirm one last time that the address highlighted in green is in fact the address that you want the coins sent to. But he started instead with the simplest of questions: Paste that into the Neo blockchain explorer. Blockchain, the key technology behind Bitcoin, is a new network that helps decentralize trade, and allows for more peer-to-peer transactions. Elena Lacey.