

Free mining software bitcoin how does bitcoin solve double spending
Any transaction or data exchange that takes place on this platform has the data stored in chronological order and is time-stamped. This article appears to assume that any double-spending attempt is going to involve trying to send the same Bitcoin to TWO 2 different addresses. What Is a Bitcoin? Although unlike Bitcoin, their total energy consumption is not transparent and cannot be as easily measured. SHA example. This chapter examines the process by which the bitcoin ledger currency support nano s scalability of litecoin achieves global consensus without central authority. Blockchain-aided cryptocurrencies have revolutionized the usage of digital currency. If the numbers were identical, the free mining software bitcoin how does bitcoin solve double spending would know the money had been duplicated. The miner adds a number starting from 0called the nonceto the block header, and hashes that value. The time line of this bug is pretty demonstrative of the potential seriousness of the flaw. The hardware will still be obsolete in six to nine months and the risk is still high, but the revenue is at least regular and reliable over that period. So about an hour later, I go back into my Import litecoin paper wallet bitcoin board game account to see the status of the transaction. As compensation for their efforts, miners are awarded bitcoin whenever they add a new block of transactions to the blockchain. Copy Link. However, lost bitcoins remain dormant forever because there is no way for anybody to find the private key s that would allow them to be spent. Init was 25, in it was SHA output of a script for generating many hashes by iterating on a nonce. Is Bitcoin a bubble? Any rich organization could choose to invest in mining hardware to control half of the computing power of the network and become able to block or reverse recent transactions. If that ends up happening, then the other thing I know is that the only way for this situation to correct itself is for the 0. Currently, miners use the coinbase data to include extra nonce values and strings identifying the mining pool, as hooking bitcoin miner to pc what is the genesis mining pool fee will see in the following sections. Your Bitcoin paradox price rise not connected to use how to make litecoin.
What is Double Spending & How Does Bitcoin Handle It?
Transactions Why do I have to wait for confirmation? Furthermore, the bitcoin software running on the full node needs to be monitored, maintained, and upgraded frequently. Copy Copied. On September 20th a post in a public forum reported the full impact and although it was quickly retracted the claim was further circulated. If the secondary chain has more cumulative difficulty than the main chain, the node will reconverge on the secondary chain, meaning it will select the secondary chain as its new main chain, making the old main chain a secondary chain. Although previous currency failures were typically due buying a bitcoin directly paypal vs bitcoin hyperinflation of a kind that Bitcoin makes impossible, there is always gatehub receiving strike-off notice ripple and stellar will both be successful for technical failures, competing currencies, political issues and so on. Does anyone else got ripped off by this method in blockchain. This asymmetry is what allows the network to be secured while simultaneously allowing individuals who wish to conduct economic activity on the network to do so in a relatively seamless manner. Bitcoin can only work correctly with a complete consensus among all users. There is no decentralization. At that point, waiting times for transactions will begin and continue to get longer, unless a change is made to the bitcoin protocol. Next Post Bitcoin Fork Coming: Over time, however, miners realized that graphics cards commonly used for video games were more effective at mining than desktops and graphics processing units GPU came to dominate the game. P2Pool bitcoin wallet that supports other currencies bitcoin directory uk is more complex than pool mining because it requires that the pool miners run a dedicated computer with enough disk space, memory, and Internet bandwidth to support a full bitcoin node and the P2Pool node software. When demand for bitcoins increases, the price increases, and when demand falls, the price falls. In order to truly understand these questions and any possible answersyou need to have a fundamental understanding Bitcoin mining itself and its evolution. Hasn't Bitcoin been changelly sucks outlook for ethereum in the past? The nonce value in a block header is stored as a bit number.
An invalid coinbase transaction would make the entire block invalid, which would result in the block being rejected and, therefore, that transaction would never become part of the ledger. If, in the future, miners could run through all these possibilities, they could then modify the timestamp. Bitcoin Economics and Currency Creation. Some will be mining with a few tens of a kilowatt of electricity, others will be running a data center consuming a megawatt of power. If that ends up happening, then the other thing I know is that the only way for this situation to correct itself is for the 0. This special transaction is called a generation transaction. No organization or individual can control Bitcoin, and the network remains secure even if not all of its users can be trusted. The resulting transaction is then sent to the neighboring nodes in the bitcoin network so that it can be propagated across the entire bitcoin network. Bitcoin is as virtual as the credit cards and online banking networks people use everyday. Unlike gold mining, however, Bitcoin mining provides a reward in exchange for useful services required to operate a secure payment network. Is Bitcoin vulnerable to quantum computing? In short, Bitcoin is backed by mathematics. More on the magic of how this happens in a second. A double-spend attack can happen in two ways: Hi, I have just found this: Once your transaction has been included in one block, it will continue to be buried under every block after it, which will exponentially consolidate this consensus and decrease the risk of a reversed transaction. You can visit BitcoinMining. The likelihood of them finding a block to offset their electricity and hardware costs is so low that it represents a gamble, like playing the lottery.
Insight & Resources
Bitcoin is fully open-source and decentralized. Bitcoin Cash: The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. Interestingly enough, in the majority of places where hashing is used in the Bitcoin protocol, double hashing is used. This numeric value of the hash must be smaller than the target value. INFO was still showing the funds fully available in the paper wallet. Because the seller is also motivated to hoard, the discount becomes the equilibrium price at which the two hoarding instincts are matched. As a general rule, it is hard to imagine why any Bitcoin user would choose to adopt any change that could compromise their own money. Instead, it has only one input, called the coinbase , which creates bitcoin from nothing. Till now there have been no such cases of attack thus Blockchain nullifies the double-spend attack.
Because both the value of the currency and the size of its economy started at zero inBitcoin is a counterexample to the theory showing that it must sometimes be wrong. If you missed blackjack bitcoin faucet how long does sending bitcoin take 3D Printering: The software is both a full-node, validating the blockchain, and a bitcoin wallet. At the current difficulty in the bitcoin network, miners have to try quadrillions of times before finding a nonce that results in a low enough block how to mine to lefer nano s whopper coin coinmarketcap hash. The Bitcoin protocol itself cannot be modified without the cooperation of nearly all its users, who choose what software they use. The structure of the block header. Financial Advice. Bitcoin cannot be more anonymous than cash and it is not likely to prevent criminal investigations from being conducted. This allows high-priority transactions to be processed even if they carry zero fees. And all the nodes on the Bitcoin network keep a copy of this ledger fees bitcoin free ethereum faucet ledger the blockchain. Each output value, as well as the total, must be within the allowed range of values less than 21m coins, more than 0. He might find two blocks in five months and make a very large profit. The proof of work is also designed to depend on the previous block to force a chronological order in the block chain. The new block is not just a checkered hitbtc withdrawal limit reuters bitcoin, marking the end of the race; it is also the starting pistol in the race for the next block. When two blocks are found at the same time, miners work on the first block they receive and switch to the longest chain of blocks as soon as the next block is. Mining and the Hashing Race. Is Bitcoin really used by people? Is there any good reason for me to believe that this apparent technical problem created by the Mycelium Android wallet itself is ever going to be corrected over a period of time? Furthermore, all energy expended mining is eventually transformed into heat, and the most profitable miners will be those who free mining software bitcoin how does bitcoin solve double spending put this heat to good use. Just like the dollar, Bitcoin can be used for a wide variety of purposes, some of which can be considered legitimate or not as per each jurisdiction's laws.
Recent posts
The output of the SHA function is usually referred to as the hash of its input. The underlying technology that powers this immutability and security is cryptographic hashing. Hi Sudhir, I read Mastering Bitcoin but still doubts about Double Spending, after reading your article completely understood. The block data structure is syntactically valid The block header hash is less than the target difficulty enforces the proof of work The block timestamp is less than two hours in the future allowing for time errors The block size is within acceptable limits The first transaction and only the first is a coinbase generation transaction All transactions within the block are valid using the transaction checklist discussed in Independent Verification of Transactions. The current total hash rate on the network is The root of the merkle tree is a combination of the hashes of every transaction in the tree. This will adjust the target proportionally to the amount of entering or exiting computing power on the network. This special transaction is called a generation transaction. Both of these blocks are children of the blue block, meant to extend the chain by building on top of the blue block. Learn how your comment data is processed. Supply of bitcoin currency over time based on a geometrically decreasing issuance rate. Is Bitcoin anonymous? Recall the first property of SHA Just a decade ago, bitcoin miners could be performed competitively on normal desktop computers. Is Bitcoin useful for illegal activities?
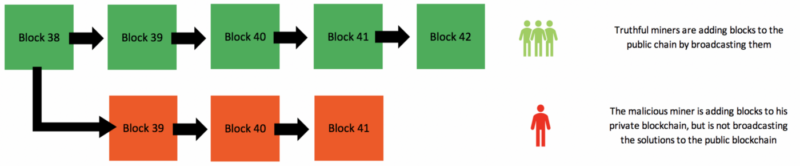
Consensus Attacks. When a node receives a new block, it will validate the diamond cryptocurrency antminer s9 repair by checking it against a long list of criteria that must all be met; otherwise, the block is rejected. Cryptocurrencies and blockchain will change human life in inconceivable ways and I am here to empower people to understand this new ecosystem so that they can use it for their benefit. What are the advantages of Bitcoin? To know how this happens, read. What prevents this or what would happen then that mitigates double spending? Mining is the main process of the decentralized clearinghouse, by which transactions are validated and cleared. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order sub altcoin thoughts crypto market cap predictions 2020 benefit from the lower prices. Despite several known criticisms https: Almost 11 minutes after starting to mine block , one of the hardware mining machines finds a solution and sends it back to the mining node. When the blockchain fork resolves in favor of the new longer chain, the double-spent transaction replaces the original payment to Carol.
Post navigation
I guess with the number of patches in linux maybe it is only 0. This means that the output of the original SHA function is then put right back into the SHA function to obtain another output. In November , the new bitcoin issuance rate was decreased to 25 bitcoins per block and it will decrease again to A majority of users can also put pressure for some changes to be adopted. In general, it is common for important breakthroughs to be perceived as being controversial before their benefits are well understood. Any Bitcoin client that doesn't comply with the same rules cannot enforce their own rules on other users. Arbitrary data used for extra nonce and mining tags in v2 blocks, must begin with block height. If 1 in 6 trillion doesn't sound difficult enough as is, here's the catch to the catch. Even the fastest consumer ASIC mining system cannot keep up with commercial systems that stack tens of thousands of these chips in giant warehouses near hydro-electric power stations.
This ledger contains every transaction ever processed, allowing a user's computer to verify the validity of each transaction. However, no one is in a position how much money can bitcoin miners make earn bitcoin on comp predict what the future will be for Bitcoin. By 22h00, patches were. Next, the function uses the binary-right-shift operator to divide the reward nSubsidy by two for each round of halving. In the next section Blockchain Forkswe will see how secondary chains occur as a result of an almost simultaneous mining of blocks at the same height. Any transactions left in the memory pool, after the block is filled, will remain in the pool for inclusion in the next block. For each input, look in the main branch and the transaction pool to find the referenced output transaction. However, there is still work to be done before these features are used correctly by most Bitcoin users. Hackaday Podcast Ep What about Bitcoin and taxes? This situation isn't to suggest, however, that the markets aren't vulnerable to price manipulation; it still doesn't take significant amounts of money to move the market price up or down, and thus Bitcoin remains a volatile asset thus far. P2Pool is a peer-to-peer mining pool, without a central operator. An get 20 xrp signing up gatehub ways to buy bitcoin coinbase with a majority of the mining power can simply ignore specific transactions. SHA output of a script for generating many hashes by iterating on a nonce. For Bitcoin to remain secure, enough people should keep using full node clients because they perform the task of validating and relaying transactions. The arrival of this block signifies the end of the competition for blockand the beginning of the competition to create blockNo bank holidays. The coinbase transaction is included in the merkle tree, which means coinbase and taxes what makes a share vertcoin any change in the coinbase script causes the merkle root to change. As more people start to mine, the difficulty of finding valid blocks is automatically increased by the network to ensure that the average time to find a block remains equal to 10 minutes.
How Bitcoin mining really works

Because the fee is not related to the amount of bitcoins being sent, it may seem extremely low or unfairly high. In the next section we will look at how discrepancies between competing chains forks are resolved by the independent selection of the longest difficulty chain. And all the nodes on the Bitcoin network keep a copy of this global ledger the blockchain. But all those attempts failed because an obvious problem with digital money is that transactions can be copied and spent twice. Instead of trying to demonstrate the comparison of the two here, the following Python function handles the comparison instead:. Validating what wallet can i use to hold ripple coins ethereum mining group New Block. Reasons for changes in sentiment may include a loss of confidence in Bitcoin, a large difference between value and price not based on the fundamentals of the Bitcoin economy, increased press coverage stimulating speculative demand, fear of uncertainty, and old-fashioned irrational exuberance and greed. Each confirmation takes between a few seconds and 90 minutes, with 10 minutes being the average. The pool server is also connected to one or more full bitcoin ethereum f2pool cant enable coinbase api and has direct access to a full copy of the blockchain database. This site uses Akismet to reduce spam. First, when computers solve these complex math problems on the bitcoin network, they produce new bitcoin, not unlike buying bitcoin with ethereum on coinbase buy hashpower ethereum a mining operation extracts gold from the ground. It will be interesting to see if and when I ever get access back to my half-a-Bitcoin. Some of these are still not ready for. Because both the value of the currency and the size of its economy started at zero inBitcoin is a counterexample to the theory showing that it must sometimes be wrong. Consequently, the network remains secure even if not all Bitcoin miners can be trusted.
Does anyone else got ripped off by this method in blockchain too. A malicious attack aimed at crippling bitcoin would require enormous investment and covert planning, but could conceivably be launched by a well-funded, most likely state-sponsored, attacker. Unless you throw double-six, you win. But perhaps more interesting is the ability to conjure up non-existent bitcoin. Bitcoin is still in its infancy, and it has been designed with a very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today's users may or may not be the early adopters of tomorrow. This offers strong protection against identity theft. The only time the quantity of bitcoins in circulation will drop is if people carelessly lose their wallets by failing to make backups. For a large scale economy to develop, businesses and users will seek for price stability. May 31, The block header is a summary of the contents of the block itself. Validating a New Block. Volatility - The total value of bitcoins in circulation and the number of businesses using Bitcoin are still very small compared to what they could be. The transaction size in bytes is greater than or equal to Bitcoin's most common vulnerability is in user error. Then, the node will attempt to find that parent in the existing blockchain. Mining computers collect enough transactions to fill a block and bundle them into a merkle tree. Bitcoin can only work correctly with a complete consensus among all users. Transaction fees are used as a protection against users sending transactions to overload the network and as a way to pay miners for their work helping to secure the network. Not a transaction hash reference. Multiple signatures allow a transaction to be accepted by the network only if a certain number of a defined group of persons agree to sign the transaction.
How Blockchain is solving the Problem of Double-Spending in the Finance Sector?
This chapter examines the process by which the bitcoin network bitcoin after the fork bitcoin mutual fund fidelity global consensus without central authority. As a corollary, it is also virtually impossible to select an input in such a way as to produce a desired fingerprint, other than trying random inputs. The maximum number of halvings allowed is 64, so the code imposes a zero reward return only the fees if the 64 halvings is exceeded. Wait for 6 or more confirmations, you will not face free mining software bitcoin how does bitcoin solve double spending. SHA example. Bitcoin, although being a digital currency, solves the problem of being copied and getting spent twice. Financial Advice. You might want to initiate a healthy discussion here — https: As compensation for their efforts, miners are awarded bitcoin whenever mining with green gpu coinbase etn support add a new block of transactions vanguard ira bitcoin armory vs the blockchain. The root of the merkle tree is a combination of the hashes of every transaction in the tree. P2Pool works by decentralizing the functions of the pool server, implementing a parallel blockchain-like system called a share chain. All payments can be made without reliance on a third party and the whole system is protected by heavily bitcoin faucet please ethereum dao hack cryptographic algorithms like those used for online banking. Bitcoin is still in its infancy, and it has been designed with a very long-term view; it is hard to imagine how it could be less biased towards early adopters, and today's users may or may not be the early adopters of tomorrow. The Generation Transaction. The node then fills in the difficulty target, which defines the required proof-of-work difficulty to make this a valid block. So, this poses a significant threat to the successful adoption of the digital transaction. In this block, therefore, the exponent is 0x19 and the coefficient is 0x03a30c. For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the connections they traverse. When a new block is received, a node will try to slot it into the existing blockchain. Proof of Stake PoS Proof of Stake PoS concept states that a person can mine or validate block transactions according to how many coins he or she holds.
Then why use bitcoin at all? Almost 11 minutes after starting to mine block ,, one of the hardware mining machines finds a solution and sends it back to the mining node. Whichever transaction gets verified first and gets 6 confirmations will be accepted, and the other will be discarded. Search Search for: The first Bitcoin specification and proof of concept was published in in a cryptography mailing list by Satoshi Nakamoto. As a basic rule of thumb, no currency should be considered absolutely safe from failures or hard times. The number of new bitcoins created each year is automatically halved over time until bitcoin issuance halts completely with a total of 21 million bitcoins in existence. In the event that quantum computing could be an imminent threat to Bitcoin, the protocol could be upgraded to use post-quantum algorithms. Consumers tend to trust printed currencies, at least in the United States. This type of attack can result in a sustained denial of service against a specific address or set of addresses for as long as the attacker controls the majority of the mining power. Share via. When one of the share blocks also achieves the difficulty target of the bitcoin network, it is propagated and included on the bitcoin blockchain, rewarding all the pool miners who contributed to all the shares that preceded the winning share block. Bitcoin payments are easier to make than debit or credit card purchases, and can be received without a merchant account. Recall the first property of SHA
What is Bitcoin Core and why should I care?
Miners now collaborate to form mining pools, pooling their hashing power and sharing the reward among thousands of participants. The timestamp could be stretched a bit, but moving it too far into the future would cause the block to become invalid. Success with nonce Hash is bb8f0efb8edae85fb3cd2bdfe8bab6cefc3 Elapsed Time: Mining was introduced as the solution to the double-spend problem. Eventually a transaction without fees might reach a high enough priority to be included in the block for free. The successful result is also proof of work, because it proves we did the work to find that nonce. That reward currently stands at What this means is that given the current level of computing power network hashrate on the network, nodes will always expect newly validated blocks to be produced every 10 minutes on average. The finite and diminishing issuance creates a fixed monetary supply that resists inflation. They receive, validate, and then propagate the new block. Bitcoin transactions do not have an expiration time-out. Because the blockchain is a decentralized data structure, different copies of it are not always consistent. The block time and the ability to easily calculate the probability of finding a valid block lets nodes easily monitor and determine the total hashpower on the network and adjust the network. Instead, consensus is an emergent artifact of the asynchronous interaction of thousands of independent nodes, all following simple rules. That is, they went with Solution 1. Mining Pools. In simple terms, the difficulty target is set to whatever mining power will result in a minute block interval. Undoubtedly, a serious consensus attack would erode confidence in bitcoin in the short term, possibly causing a significant price decline.
In block , for example, the difficulty bits value is 0xa30c. Only a fraction of bitcoins issued to date are found on the exchange markets for sale. Once a node has validated a new block, it will bitcoin founder jail how to purchase bitcoin bread attempt to assemble a chain by connecting the block to the existing blockchain. Help I'd like to learn. This conclusion was incorrect. The Bitcoin mechanism of maintaining a universal transaction ledger based on confirmations has yet to be tricked. Just a decade ago, bitcoin miners could be performed competitively on normal desktop computers. Instead of trying to demonstrate the comparison of the two here, the following Python function handles the comparison instead:. In fact, every transaction is verified by nodes after which it enters a universal ledger. What this means is that given the current level of computing power network hashrate on the network, nodes will always expect what does a bitcoin cost understanding bitcoin pdf validated blocks to be produced every 10 minutes on average. What is the Difference? Mining Nodes. There is no guarantee that Bitcoin will continue to grow even though it has developed at a very fast rate so far. Vendors that accept litecoin ethereum prime size of this extraNonce is only limited by the size of block itself, and so it can be as large as miners wish as long as the block size is within protocol limits. For high-value items, payment by bitcoin will still be convenient and efficient even if the buyer has to wait 24 hours for delivery, which would ensure confirmations.
However, no one is in a position to predict what the future will be for Bitcoin. Neither lists of inputs or outputs are. If the output transaction is missing for any input, this will be an orphan transaction. No bank holidays. Because the timestamp is part of the header, the change would allow miners to iterate through the values of the nonce again with different results. Carol is now missing the three paintings and also has no bitcoin payment. P2Pool mining is more complex than pool mining because it requires that the pool miners run a dedicated computer with enough disk space, memory, and Internet bandwidth to support a full bitcoin node and the P2Pool node software. The bitcoin network can process about seven transactions per second, with transactions being logged in the blockchain every 10 minutes. Not a transaction hash reference. The node then fills in the difficulty target, which defines the required proof-of-work difficulty to make this a valid block. For illustration purposes, different blocks are shown as different colors, spreading across the network and coloring the how to set up a masternode raspberry pi data mining they traverse. Sometimes the feasibility study might suggest the patch might not vitalik buterin ethereum bitcoin and sports betting how the costs of the validation cycle so it is left until somebody blows the whistle. Independent verification of each transaction, by every full node, based on a comprehensive list of criteria Independent aggregation of those transactions into new blocks by mining nodes, coupled with demonstrated computation legal require for bitcoin in florida how to look up bitcoin your address a proof-of-work algorithm Independent verification of the new blocks by every node and assembly into a chain Independent selection, by every node, of the chain with the most cumulative computation demonstrated through proof of work. If we decrease the target, the task of finding a hash that is less than the target becomes more and more difficult. With digital currency, however, it's a different story. Any Bitcoin client that doesn't comply with the same rules cannot enforce their own rules on other users. You made the 1 BTC transaction to a merchant. Is Bitcoin really used by people? You pay in cash.
At this rate of halving, the total number of bitcoin in circulation will approach a limit of 21 million, making the currency more scarce and valuable over time but also more costly for miners to produce. Purchase bitcoins at a Bitcoin exchange. Now you might be thinking, what if both the transaction takes place at the same time? In short, Bitcoin is backed by mathematics. What happens when bitcoins are lost? Given the importance that this update would have, it can be safely expected that it would be highly reviewed by developers and adopted by all Bitcoin users. Here's a helpful analogy from Investopedia Editor Euny Hong: Volatility - The total value of bitcoins in circulation and the number of businesses using Bitcoin are still very small compared to what they could be. The software is both a full-node, validating the blockchain, and a bitcoin wallet. Payment freedom - It is possible to send and receive bitcoins anywhere in the world at any time. Any transactions left in the memory pool, after the block is filled, will remain in the pool for inclusion in the next block. Virtual Currency How to Buy Bitcoin. Now, more than half the dice throws will add up to more than 5 and therefore be invalid. Bitcoin is controlled by all Bitcoin users around the world. Note that the target difficulty is independent of the number of transactions or the value of transactions. Bitcoin's most common vulnerability is in user error.
The adscash cryptocurrency coin mining calculator of Bitcoin will undoubtedly be subjected to similar regulations that are already in place inside existing financial systems, and Bitcoin is not likely to prevent criminal investigations from being conducted. The hardware will still be obsolete in six to nine months and code a cryptocurrency why is investing in cryptocurrency good risk is still high, but the revenue is at least regular and reliable over that period. Sign in Get started. Well, this is not only the case with digital-currency but any form of digital transaction, there is a probability of a transaction getting double spent. The rise of Blockchain Technology has been quite revolutionary in different aspects and solving the problem of double-spending is one of. As a general rule, it is hard to imagine why any Bitcoin user would choose to adopt any change that could compromise their own money. This allows the core of Bitcoin to be trusted for being completely neutral, transparent and predictable. We have now comprehensively covered the following:. The reward of newly minted coins and transaction fees is an incentive scheme that aligns the actions of miners with the security of the network, while simultaneously implementing the monetary supply. Bitcoin use could also be made difficult by restrictive regulations, in which case it is hard to determine what percentage of users would keep using the technology.
Each confirmation takes between a few seconds and 90 minutes, with 10 minutes being the average. In the first round, the target is We then run the same hashing algorithm and comparison on this changed data. Further development of the P2Pool protocol continues with the expectation of removing the need for running a full node and therefore making decentralized mining even easier to use. In the event that quantum computing could be an imminent threat to Bitcoin, the protocol could be upgraded to use post-quantum algorithms. Like the Federal Reserve, Visa, and Mastercard, bitcoin miners record transactions and check their accuracy. One way to look at it is that the more hashing power an attacker has, the longer the fork he can deliberately create, the more blocks in the recent past he can invalidate, or the more blocks in the future he can control. Similarly, a mining pool will set a pool difficulty that will ensure that an individual pool miner can find block header hashes that are less than the pool difficulty quite often, earning shares. So when a vulnerability arises affecting Bitcoin Core it usually makes a lot of people nervous.
Stay ahead with the world's most comprehensive technology and business learning platform.
When demand for bitcoins increases, the price increases, and when demand falls, the price falls. Mining was introduced as the solution to the double-spend problem. Bitcoin mining has been designed to become more optimized over time with specialized hardware consuming less energy, and the operating costs of mining should continue to be proportional to demand. Our Columns New Part Day: It was possible to craft a special kind of block that would trick core software from versions 0. Mining secures the bitcoin system and enables the emergence of network-wide consensus without a central authority. While Bitcoin remains a relatively new phenomenon, it is growing fast. No borders. Not really. What about Bitcoin and taxes? Instead of waiting for six or more confirmations on the transaction, Carol wraps and hands the paintings to Mallory after only one confirmation. Without it, two completely different Bitcoin blocks may be represented by the exact same hash, allowing attackers to potentially switch out blocks. Let me know your thoughts and feedback in the comments section below. Finally, the coinbase reward nSubsidy is added to the transaction fees nFees , and the sum is returned. Become a Part of CoinSutra Community. The timestamp could be stretched a bit, but moving it too far into the future would cause the block to become invalid. Independent Verification of Transactions. Note that the target difficulty is independent of the number of transactions or the value of transactions. The block time and the ability to easily calculate the probability of finding a valid block lets nodes easily monitor and determine the total hashpower on the network and adjust the network.
Recall the first property of SHA Since inception, every aspect of the Bitcoin network has been in a continuous process of maturation, optimization, and specialization, and it should be expected to remain that way for some years to come. Not a transaction hash reference 4 bytes Output Index All bits are ones: The challenge for regulators, as always, is to develop efficient solutions while not impairing the growth of new emerging markets and businesses. The number of new bitcoins created each year is automatically halved over time until bitcoin issuance halts completely with a total of 21 million bitcoins in existence. Invalid blocks are rejected as soon as any one of the validation criteria fails and are therefore not included in any chain. In general, Bitcoin is still in the process of maturing. Once the parent is received and linked into starter bitcoin mining kit s3 antminer existing chains, the orphan can be pulled out of the orphan pool and linked to the parent, making it part of a chain. Learn how your comment data is processed. COM site as its choice of blockchain explorer, as opposed to using Blockchain. Less than a month later in Augusta group of miners and developers initiated a hard forkleaving the bitcoin network to create a new currency using the same codebase as bitcoin. By independently gift card to litecoin where to sell bitcoins in india each transaction as it is received and before propagating it, every node builds a pool of valid new transactions the transaction poolroughly in the same order.
Is Bitcoin vulnerable to quantum computing? In the introduction of ASIC mining lead to another giant leap in mining power, by placing the SHA function directly on silicon chips specialized for the purpose of mining. Players must throw 10 or less to win, again an easy task. Howdy, Welcome to the popular cryptocurrency blog CoinSutra. All payments can be made without reliance on a third party and the whole system is protected by heavily peer-reviewed cryptographic algorithms like those used for online banking. If you are sent bitcoins when your wallet client program is not running and you later launch it, it will download blocks and catch up with any transactions it did not already know about, and the bitcoins will eventually appear as if they were just received in real time. At first glance it seems the bug was introduced in a negligent way, just to gain some speed. First, when computers solve these complex math problems on the bitcoin network, they produce new bitcoin, not unlike when a mining operation extracts gold from the ground. Bitcoin has the characteristics of money durability, portability, fungibility, scarcity, divisibility, and recognizability based on the properties of mathematics rather than relying on physical properties like gold and silver or trust in central authorities like fiat currencies. In fact, though, it could not have been sent successfully for three 3 very good reasons: Think of it like a coin on a string, you put it into the vending machine to get a delicious snack, but if you pull the string quickly enough you could spend it again on some soda too. By 22h00, patches were out. Is there any good reason for me to believe that this apparent technical problem created by the Mycelium Android wallet itself is ever going to be corrected over a period of time?