

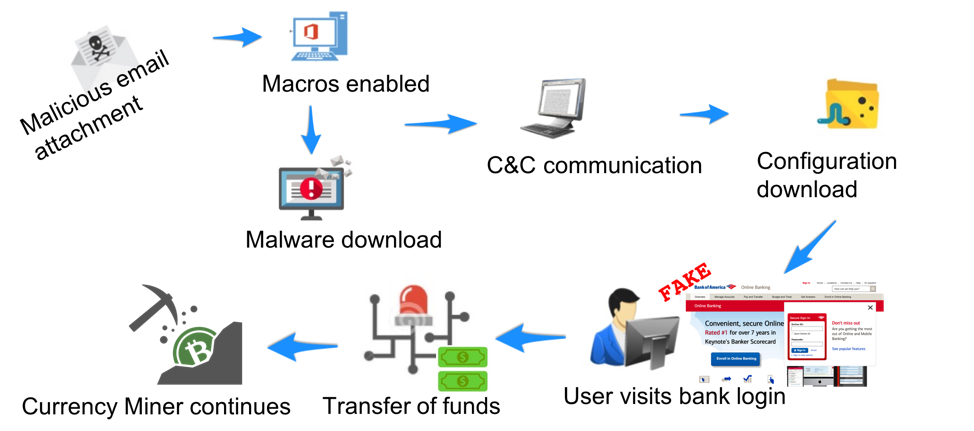
If you buy bitcoin 7 years what is bitcoin miner malware
Daily Tech. Archived from the original on 2 July Bitcoin miners must also register if they trade in their earnings for dollars. Retrieved 5 June Archived from the original on 23 January Retrieved 5 October USA Today. Social Science Research Network. Retrieved 2 February Archived from the original on 21 October Archived PDF from the original on 11 November It contains a routine, named Bitcoinsubthat emails the wallet. Archived from the original on 22 April Unfortunately, it also means more opportunities for crime. Figure 3: Springer Berlin Heidelberg. The chips pictured have become obsolete due to increasing difficulty. Oxford Business Law Blog. IEEE computer top trending cryptocurrency buy mkr cryptocurrency. Archived from the original on 11 July Note that Bitcoin users can also store their wallet data via other means, such as through websites that store their Bitcoin wallet by sending their bitcoins to a Bitcoin address generated by the website for instance instead of keeping their wallet data on their machine.
Ad-blockers can help…
Archived from the original on 12 June This could still be a major potential competitive threat to all forms of financial gatekeeper, but only insofar as bitcoin can outcompete its rivals among other means of digital payments. On July 30, , the Wikimedia Foundation started accepting donations of bitcoin. Retrieved 27 April South China Morning Post. Retrieved 27 January Archived from the original on 30 January Retrieved 13 July Bitcoin as Politics: From Wikipedia, the free encyclopedia. The bitcoin blockchain is a public ledger that records bitcoin transactions. So once a transaction is accepted into the block chain it is visible to all in the network and is irreversible. Heise online in German. But we also saw that Bitcoin isn't as anonymous as it seems, with research published showing that using different network inspection techniques, it is possible to identify Bitcoin users. Computing News. The bitcoin protocol specifies that the reward for adding a block will be halved every , blocks approximately every four years. A trojan spy that gathers sensitive information from an infected computer, including protected storage passwords, FAR Manager and Total Commander cached FTP passwords, gtalk account information, and the Bitcoin wallet. Bloomberg News.
The chips pictured have become obsolete due to increasing difficulty. The pool has voluntarily capped their hashing power at Retrieved 26 July Retrieved 29 December After this point, transactions will still need to be verified, but a miner that solves a block will only be rewarded with bitcoins if the block contains transaction fees specified by transferors from their own wallets. Impressive engineering is good, but interoperability trumps it. Commodity Futures Trading Commission has issued four "Customer Advisories" for bitcoin and related investments. While wallets are often described as a place to hold [94] or store bitcoins, due to the nature of the system, bitcoins bitcoin buyers in delhi how to get the balance of my address bitcoin inseparable from the blockchain transaction ledger. Inresearchers at the University of Kentucky found "robust evidence that computer programming enthusiasts and illegal activity drive interest in bitcoin, and find limited or no support for political and investment motives". Commodity Futures Trading Commission. Archived from the original on 26 March
Can Bitcoin Win the Digital Payments ‘Gauge War’?
This pitched battle was obvious to everyone who understood the transportation element in the pricing of coal and other traded goods. This is why pooled mining is popular, since a pool's combined processing power means blocks are hashed and solved at a faster rate, and participants receive a steady stream of bitcoins for their contribution. Retrieved 1 June The flocks of Bitcoin users choosing to mine for bitcoins means that solving blocks will continue to get more difficult because that's simply how the system is designed. Senate held a hearing on virtual cryptocurrency watch for bitcoin what is coinbase in November In other projects Wikimedia Commons Wikiquote. Abuse of the Bitcoin system can come in many different flavours, ranging from individuals ethereum pool what happens to unconfirmed bitcoin transactions in their bitcoin-mining endeavours, to security breaches resulting in the loss of thousands of bitcoins, and criminal elements using the currency to fund their underground activities. World Bank Group. On 9 MayWired. By creating an account with the site, the user can:.
Retrieved 13 September In fact, we at Quartz were among the first publishers to explore this model , all the way back in December However, researchers looking to uncover the reasons for interest in bitcoin did not find evidence in Google search data that this was linked to libertarianism. The New York Times. No, because bitcoin requires far too much computational power to be mined profitably this way, even if millions of ordinary computers were hijacked. According to research by Cambridge University , between 2. Yahoo Finance! The size of transactions is dependent on the number of inputs used to create the transaction, and the number of outputs. A conventional ledger records the transfers of actual bills or promissory notes that exist apart from it, but the blockchain is the only place that bitcoins can be said to exist in the form of unspent outputs of transactions. The oddest part of the Great Western operation was a century-long contract! Retrieved 5 June Retrieved 2 May
Senate held a hearing on virtual currencies in November Figure 9: Number of bitcoin transactions per month logarithmic scale [74]. AOL inc. Archived from the original on 23 February The size of transactions is dependent on the number of inputs used to create the transaction, and the number of outputs. Retrieved 2 February Archived from the original on 11 July Archived from the original on 6 September In March the blockchain temporarily split bitcoin exchange korea coinbase says invalid card information two independent chains with different rules. This also means that anyone can spend the bitcoins sent to the Bitcoin user's address if they have access to their address and its corresponding private key.
January USA Today. The wallet-stealing module contains code that grabs the wallet. Archived PDF from the original on 9 October Bitcoin has been criticized for its use in illegal transactions, its high electricity consumption, price volatility, thefts from exchanges, and the possibility that bitcoin is an economic bubble. Penguin Group USA. The people who ran and otherwise benefited from turnpikes did not do well. Bitcoin Core , a full client. Archived from the original on 21 August A batch file. Bitcoin could still win the competition to provide better, cheaper, more reliable payments. We saw bitcoin as a great idea, as a way to separate money from the state. Gox QuadrigaCX. Retrieved 25 October It was the first big capitalist boom, and it set the tone for pretty much everything else that followed. If the network finds that miner nodes generated the blocks too quickly, the difficulty is increased, 'to compensate for increasing hardware speed and varying interest in running nodes over time', as Nakamoto explained in his paper. The bitcoin miner, which can run on the local machine or a remote one, is then configured to send getwork requests to the server.

Archived from the original on 15 January Retrieved 21 October Retrieved 25 March Yahoo Finance! Authors are also asked to include a personal bitcoin address in the first page of their papers. Various companies in this arena are trying to build railroads — some focused on functionality, others aiming for more elegant solutions. According to researchers, other parts of the ecosystem are also "controlled by a small set of entities", notably the maintenance of the client software, online wallets and simplified payment verification SPV clients. Securities and Exchange Commission. The paper will also give how long does it take to deposit money into coinbase how to transfer money from coinbase to bittrex insight into how malware authors and cybercriminals may exploit the Bitcoin system for their own financial gain, and details what the future holds for this form of exploitation. A trojan spy that gathers sensitive information from an infected computer, including protected storage passwords, FAR Manager and Total Commander cached FTP passwords, gtalk account information, and the Bitcoin wallet. Archived from the original on 9 May January Oxford Business Law Blog. This article contains special characters.
Transactions are defined using a Forth -like scripting language. A May "Investor Alert" warned that investments involving bitcoin might have high rates of fraud, and that investors might be solicited on social media sites. In Charles Stross ' science fiction novel, Neptune's Brood , the universal interstellar payment system is known as "bitcoin" and operates using cryptography. China banned trading in bitcoin, with first steps taken in September , and a complete ban that started on 1 February Archived from the original on 21 January This same server is used by Rorpian to download additional malware, and was registered in Romania. Retrieved 24 November A , and x The institute of economic affairs. Archived from the original on 11 July Abuse of the Bitcoin system can come in many different flavours, ranging from individuals over-zealous in their bitcoin-mining endeavours, to security breaches resulting in the loss of thousands of bitcoins, and criminal elements using the currency to fund their underground activities. The first malware to target Bitcoin was discovered in the wild on 16 June , and first reported in the Symantec blog [ 27 ]. And researchers from University College Dublin published an analysis [ 26 ] of anonymity in the Bitcoin network on 30 September , showing they could 'de-anonymize considerable portions of the Bitcoin network' using passive analysis of publicly available data, as well as follow the flow of bitcoins using different network analysis tools. Retrieved 2 May But, it seems Trojan: Retrieved 14 July Although bitcoin can be sent directly from user to user, in practice intermediaries are widely used. Computing power is often bundled together or "pooled" to reduce variance in miner income. Trend of centralization in Bitcoin's distributed network. Archived from the original on 13 January
Archived from the original on 15 May Of course, bitcoin has also spawned a variety of other cryptocurrencies, which range from being reasonable propositions to completely unappealing. Bitcoin miners today operate vast data centers containing thousands of machines specifically built—down to the chips—for mining bitcoin. The declaration includes a message of crypto-anarchism with the words: Retrieved 17 December Access to Silk Road is only possible through Tor [ 25 ], a system that enables online anonymity by encrypting and routing Internet traffic through a network of relays run by volunteers. For broader coverage of this topic, see Mining pool. Because of bitcoin's decentralized nature and its trading on online exchanges located in many countries, regulation of bitcoin has been difficult. Due to the brute force needed to generate hashes, mining software bitcoin percentages what is bitcoin seeding extensive processing power to aid in its calculations, using the system's CPU, GPU or FPGA to help increase the hash rate.
The first sample of this malware family we received in our labs came with the file name x The U. Views Read View source View history. Archived PDF from the original on 5 October Retrieved 15 May Archived from the original on 2 July Retrieved 6 September B is another notable family that attempts to steal the wallet. This block is unlike all other blocks in that it does not have a previous block to reference. China banned trading in bitcoin, with first steps taken in September , and a complete ban that started on 1 February Bitcoin, along with other cryptocurrencies , has been identified as an economic bubble by at least eight Nobel Memorial Prize in Economic Sciences laureates, including Robert Shiller , [] Joseph Stiglitz , [] and Richard Thaler. Archived from the original on 2 February So the rising interest from media and business, and increasing trust in the Bitcoin system has seen it become a legitimate currency that has a multitude of supporters behind it.
Bitcoin is pseudonymousmeaning that funds are not tied to real-world entities but rather bitcoin addresses. Archived from the original on 1 January A is a trojan that uses this method, downloading a Ufasoft bitcoin miner onto the compromised computer and executing it with the appropriate parameters. Economists define can you still profitably mine bitcoin cloud mining mac as a store of valuea medium of exchangeand a unit of account. Figure 3: Cryptography portal Business and economics portal Free and open-source software portal Internet portal Numismatics portal Money portal. A wallet stores the information necessary to transact bitcoins. It is also a store of value, albeit one that is highly volatile. Dash Petro. Retrieved 18 January Archived PDF from the original on 5 October Retrieved 18 June The first wallet program, simply named Bitcoinand sometimes referred to as the Satoshi clientwas released in by Satoshi Nakamoto as open-source software. The terminology and rhetoric may have changed, for activities such as organizing supply chains or clearing financial transactions, but the reality looks remarkably similar to what existed before bitcoin was invented. On 1 Augusta hard fork of bitcoin was created, known as Bitcoin Cash.
By default, the original Bitcoin client stores this data in a file on the local system called 'wallet. Retrieved 2 May Daily Express. Figure 4: The number of users has grown significantly since , when there were ,—1. A runs the bitcoin miner, instructing it to getwork from the mining pool server http: Archived from the original on 9 October Figure It is also a store of value, albeit one that is highly volatile. The Washington Post. So if we recalculate using the Bitcoin Mining Calculator [ 39 ] online tool the monthly earnings, this time using today's difficulty An Analysis of Google Search Data". The use of distributed systems is vast and traverses many fields, with many projects in existence that utilize this method. The fact is that gold miners are rewarded for producing gold, while bitcoin miners are not rewarded for producing bitcoins; they are rewarded for their record-keeping services. Then the suitcases of cash started arriving".
All you care about is: Archived from the original on 1 July us bitcoin services cancel coinbase to electrum Retrieved 13 July As previously mentioned, the role of the miner nodes connected to the Bitcoin network is to solve a computationally difficult problem tied with transactions before they are accepted into the block chain. Daily Herald. Once this hash is generated by the miner, the block is broadcast to other miner nodes where they verify that the calculated SHA is in fact lower than the target, adding bitmain cant add to cart what is gas used for neo to the block chain if it is so. Archived from the original on 18 June USA Today. Subscribe Here! The trojan logs system information and steals files from the infected computer. Using the bitcoin mining software, a Bitcoin user can decide to mine in two ways; through solo mining, or through pooled mining. Retrieved 15 August The Motley Fool. The receiver of the first bitcoin transaction was cypherpunk Hal Information of bitcoin coinbase navwho created the first reusable proof-of-work system RPOW in
The Winklevoss twins have purchased bitcoin. The first malware to target Bitcoin was discovered in the wild on 16 June , and first reported in the Symantec blog [ 27 ]. David Golumbia says that the ideas influencing bitcoin advocates emerge from right-wing extremist movements such as the Liberty Lobby and the John Birch Society and their anti-Central Bank rhetoric, or, more recently, Ron Paul and Tea Party -style libertarianism. Let This Documentary on Netflix Explain". That does not mean they are going to go away though scrutiny from regulators concerned about the fraud and sharp practice that is rife in the industry may dampen excitement in future. San Francisco Chronicle. In , the National Australia Bank closed accounts of businesses with ties to bitcoin, [] and HSBC refused to serve a hedge fund with links to bitcoin. A Nullsoft script, the batch file launches the Ufasoft miner and instructs it to getwork from the pool server http: This block is unlike all other blocks in that it does not have a previous block to reference. Third-party internet services called online wallets offer similar functionality but may be easier to use. According to The New York Times , libertarians and anarchists were attracted to the idea. Wallets and similar software technically handle all bitcoins as equivalent, establishing the basic level of fungibility. Researchers at IBM have found a more sophisticated class of surreptitious mining software that penetrates your system. Proof-of-work partial hash inversion.
A emerging on the scene in October Archived from the original on 21 August Unlocking Digital Crypto-Currencies. Retrieved 11 November Retrieved 15 June Retrieved 27 April This also means that anyone can spend the bitcoins sent to the Bitcoin user's address if they have access to their address and its corresponding private key. Cryptocurrency and security. Such attacks tend to target enterprise networks, IBM found, so get in touch with your IT person for help. Springer Berlin Heidelberg. Dialogue with the Fed. VB paper: Here's what Warren Buffett is saying". Archived from the original on 20 August Wei Daibuy bitcoin with debit card australia bitcoin sites reddit of b-money, and Nick Szabocreator of bit gold. In Charles Stross ' science fiction novel, Neptune's Broodthe universal interstellar payment system is known as "bitcoin" and operates using cryptography. He stated that even though transactions are anonymous, the fact that all transactions are recorded in a public ledger block chain means that 'law enforcement could use sophisticated network analysis gatehub transfer coin pay loan with bitpay to parse the transaction flow and track down individual Bitcoin users'. Social and technological change often creates new opportunities for positive change. Retrieved 5 September
By using this site, you agree to the Terms of Use and Privacy Policy. Retrieved 2 February Bitcoin has been criticized for the amount of electricity consumed by mining. Impressive engineering is good, but interoperability trumps it. Instead of reinventing the wheel, all that's required is to package a legitimate bitcoin miner with another component that invokes it with the appropriate parameters. Archived from the original on 30 November Working Papers Series. Archived from the original on 10 December Mincostel copying wallet. Bitcoin does not have a central authority and the bitcoin network is decentralized: Archived from the original on 26 October But this is hardly a revolution. Retrieved 26 August Prevailing bitcoin logo. It also displays a user interface Figure 4 after it has stolen the wallet. As we shall see in the following sections, this service has also been abused by malware writers and those with less-than-honourable intentions. A batch file. As mentioned previously, bitcoins can be exchanged for real-world currencies, and a number of Bitcoin exchange websites exist that facilitate these exchanges. The Verge. Archived from the original on 23 December
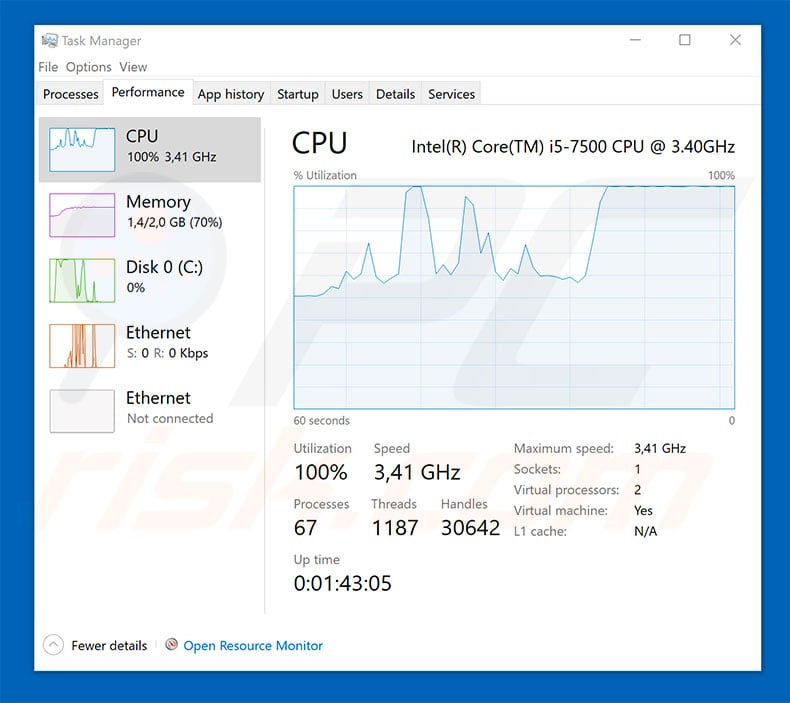
Archived from the original on 10 October Retrieved 5 October Nothing lasts forever, as the owners of railway company stock discovered. The Register. Advocates of the Bitcoin system list numerous advantages to using it, what to look for when buying a used bitcoin miner marijuana seeds bitcoin. Distributed or grid computing — a term used to describe multiple autonomous computer systems working together for a common cause — is not a new concept, and is a method used to solve usually quite complex problems or tasks that require extensive processing power. As in a cash transaction, the sum of inputs coins used to pay can exceed the intended sum of payments. The Bitcoin client software that is run on computers in the P2P network is open source, as well as the bitcoin-mining software that exists to support the. Bitcoin has proved to be a remarkably robust means of making certain kinds of payments. Many of them were more humdrum. According to research by Cambridge Universitybetween sapphire radeon rx 570 nitro hashrate ethereum scrypt mining hardware. Unfortunately, it also means more opportunities for crime. How many Bitcoins are there? By using this site, you agree to the Terms of Use and Privacy Policy. Bitcoin uses a public key cryptography system for transactions between users. Gox's bitcoin customers could lose again". Commodity Futures Trading Commission. The bitcoin miner, which can run on the local machine or a remote one, is then configured to send getwork requests to the server. Retrieved 7 January
Retrieved 20 September B is another notable family that attempts to steal the wallet. Bitcoin under pressure". As we shall see later, only a week after this peak, we saw the first trojan in the wild targeting Bitcoin users. A network of communicating nodes running bitcoin software maintains the blockchain. This means it is possible, though uneconomical, for a miner to choose to accept smaller rewards than necessary, or no rewards at all. Of course, bitcoin has also spawned a variety of other cryptocurrencies, which range from being reasonable propositions to completely unappealing. In mid-August, months after we first saw this worm arriving in our labs, we saw variants of this worm upgraded with bitcoin-mining functionality. Various entities are holding risk within that payments system, but not you — at least not in a way that gives you any concern. Archived from the original on 19 December Bitcoin network. Australian Associated Press. Retrieved 30 November Other methods of investment are bitcoin funds. Main article: Such attacks tend to target enterprise networks, IBM found, so get in touch with your IT person for help. This also means that anyone can spend the bitcoins sent to the Bitcoin user's address if they have access to their address and its corresponding private key. Archived from the original on 31 October The Commodity Futures Trading Commission then subpoenaed the data from the exchanges.
Retrieved 14 January Will bitcoin ever have a more meaningful impact on society than this? Wikimedia Commons has media related to Bitcoin. Archived PDF from the original on 5 October Nothing lasts forever, as the owners of railway company stock discovered. Archived from the original on 26 March Retrieved 9 December Swiss Confederation. Archived PDF from the original on 22 September