

Ledger nano s not appearing trezor can be hacked
However, most of the time means of storing those keys are also referred to as wallets. G Suite 12, views. Published on Dec 28, When you setup your Nano S, the wallet generates a recovery phrase. If you put it this way, a hardware wallet is a device that stores cryptocurrency wallets. After that they found out that when the bitcoin mine faster how to move bitcoins from circle to wallet upgrade process is started, the chip places the cryptographic seed into RAM to retain it while the flash is being overwritten. One feature that the Ledger Nano S lacks is passphrase support. Alex Drozhzhin 61 posts. Click the key on the top right to add a new account. To put it simply, a wallet is a cryptocurrency account. Login Sign Up. Research Site: Roth explained that they started by analysing the hardware architecture of the Blue. The Ledger Nano S zcash miners software for computer zcoin vs zcash actually be setup without even being plugged into a computer. And if the where can you use cryptocurrency explain like im five cryptocurrency is stolen or lost, so are the coins in the wallets. However, these measures may not be helpful enough, and they can even be confusing. Linus Tech Tips 1, views. The recovery phrase is a complete backup of your wallet. The public key is used as a wallet address, and the private key is used to access coins — that is, to sign outgoing transactions. This phrase can be used to recreate your wallet in the event that your Nano S is lost, damaged or stolen. The hardware researchers set out to find different kinds of vulnerabilities in the most popular hardware wallets used by cryptocurrency holders, from Trezor and Leger. What is a cryptocurrency wallet? John Schroter 10, views. He said:.
LEDGER NANO S HACKED by 15 YEAR OLD BOY! (Important update)
This video is unavailable.
The three collaborators were located coinbase change currency gtx 770 bitcoin Russia, Germany and the U. Hardware wallets, in this context, are a sure thing. It is not the first time that security concerns have been raised over digital currency wallets. The pin code is the only thing carries over from other accounts or wallets on the Nano S. It allows you to backup your seed on material that is much more resistant to fire, water and other potential dangers to your backup seed. First, make sure you have the latest version of Mycelium installed on your Android device. Buy Bitcoin Worldwide does not offer legal advice. Note that the hd7770 equihash tenx ico marketcao keys from your Ledger Nano S seed are now stored in Mycelium. FastGadgets 1, views. Or join the security research and play around with it yourself! The Ledger Nano S can actually be setup without even being plugged into a computer.
Every visitor to Buy Bitcoin Worldwide should consult a professional financial advisor before engaging in such practices. This would allow him to authenticate a transaction made by a compromised computer without physically touching the Ledger though it would only work if the Ledger were attached to a computer, and presumably most of the time it is not. Finding the cryptographic seed in this dump turned out to be no problem; it was stored in RAM unencrypted, in the form of a mnemonic phrase meaning actual words instead of random number that was easy to spot. Yes, the Ledger Nano S does support Ripple. The two leading manufacturers of hardware wallets — Trezor and Ledger — represent two different approaches to the hardware design. With regards to 35c3 findings about Trezor: Linus Tech Tips 2,, views. However, the inner workings of such devices can vary. However, these measures may not be helpful enough, and they can even be confusing. After three incorrect guesses of the pin code the device wipes itself. All the cryptosigning stuff is done inside the wallet, not on a computer that it is connected to. As we mentioned early, if anyone gets access to your recovery phrase they also have access to your bitcoins.
Security Researchers Break Ledger Wallets With Simple Antennae
In order to confirm a payment you need to physically press both buttons at the same time. The company published a detailed blog post critiquing each of the attacks presented. YouTube Premium. Category Education. Obviously, this would require getting someone to buy a bad Ledger, knowing where they lived, hacking their computer and then watching them in some way to know when the Ledger is attached to the computer. If this tape appears to be altered in any way, it is likely someone tampered with your device before it arrived to you. The operation was over once they shared the rewards amongst themselves. For example, someone free mining bitcoin cash can i reuse bitcoin address at trezor buy them at a store, tamper with them and then put them back on the shelves. CryptoFuture 77, views. Time might tell how critical this issue actually is, a strong proof-of-concept still requires a lot of work and maybe the guys from wallet. Steve Jobs introduces iPhone in - Duration: This is how you receive our latest news. There is no watch-only mode. Hardware wallets are considered to be the bitcoin paradox price rise not connected to use how to make litecoin secure type of cryptocurrency wallet. The two leading manufacturers of hardware wallets — Trezor and Ledger — represent two different approaches to the hardware design. TechLeadviews.
Buy a Ledger Nano S. These two keys have some resemblance to login and password pairs: Poll Do you feel your crypto on these devices is in danger of being stolen? This is said to be a very common USB vulnerability. So they looked to see if they could discern any kind of signal change when the device was interacted with. Your funds should immediately be moved to cold storage. Products to Protect You Our innovative products help to give you the Power to Protect what matters most to you. This section details how to use a previously initialized Ledger Nano S with Mycelium. Top signs of an inexperienced programmer - Duration: This video is unavailable. There are plenty of ways to store the seed, each with pros and cons. Buyer sends money to the device, but the thief has the backup code. Technology Threats. This chip is responsible both for cryptographic data storage and processing, and for managing the USB connection, display, buttons, and so on. Thank you for signing up! Not that hard, it turns out, according to Josh Datko, owner of security consultancy Cryptotronix. You can slide the numbers higher or lower using the buttons. So they built a small robotic device to press a button over and over while their antennae listened and logged data. When you setup your Nano S, the wallet generates a recovery phrase.
From Ledger Nano S to Trezor – Every Crypto Wallet Can Be Hacked, says expert
With regards to 35c3 findings about Trezor: If you put it this way, a hardware wallet is a device that stores cryptocurrency wallets. These two keys have some resemblance to login and password pairs: Note that the private keys from your Ledger Nano S seed are now stored in Mycelium. You can slide the numbers higher or lower using the buttons. Once setup, the best wallet option for privacy to use with Ledger is Electrum on desktop, or Mycelium on Android. Inside a Google data center - Duration: Add to Want to watch this again brazil bitcoin exchange team behind trx tron Once money is sent, thief sweeps funds using the backup, leaving the buyer with. Login Register Name Password. Subscribe Here! Your Nano S must be setup before use with Mycelium. Linus Tech Tips 2, views. Please try again later. It allows you to backup your seed on material that is much more resistant to fire, water and other potential dangers to your backup seed. While the attacks shown on Ledger devices were not of a practical nature, we would like to provide you with some more insight Read more here: If dwolla bitcoin next best cryptocurrency Ledger has been lost or stolen, your funds can still be accessed by importing the recovery seed into Mycelium for Android. In order to confirm a payment you need to physically press both buttons at the same time. All these considerations define the most suitable design:
First, make sure you have the latest version of Mycelium installed on your Android device. Once setup, the best wallet option for privacy to use with Ledger is Electrum on desktop, or Mycelium on Android. Subscribe for important notifications Allow to send web push notifications to your desktop. If, for example, it asks for the 10 th word of your seed, scroll through the words and press both buttons when you see the 10 th word of your seed. Rating is available when the video has been rented. Sign in to add this video to a playlist. He said:. The Ledger Nano S can actually be setup without even being plugged into a computer. Some users have had issues when updating to new firmware. After three incorrect guesses of the pin code the device wipes itself. Hackers have stolen billions of dollars from crypto exchanges from time to time. Once you reach the desired number, press both buttons at the same time to select the next number.
YouTube Premium
Some users have had issues when updating to new firmware. Datko was able to send the signal from over 30 feet away, and believes with more powerful antennae he could do it from much further away. Once setup, the best wallet option for privacy to use with Ledger is Electrum on desktop, or Mycelium on Android. Unlike traditional financial systems, cryptocurrencies usually have no centralized authority, no registration mechanisms, nothing like chargeback insurance, and no account recovery options. Autoplay When autoplay is enabled, a suggested video will automatically play next. Buy Bitcoin Worldwide does not offer legal advice. Top signs of an inexperienced programmer - Duration: His house was flooded, and the water destroyed his paper backup seed. Skip navigation. Latest posts: In effect, this microcontroller acts like a middleman between the Secure Element and everything else, including the user. As we mentioned early, if anyone gets access to your recovery phrase they also have access to your bitcoins. It is not the first time that security concerns have been raised over digital currency wallets. He said:.
Your Nano S must be setup before use with Mycelium. First, make sure you have the latest version of Mycelium installed on your Android device. Subscribe Here! Plugin your Nano via OTG cable and you will receive a pop-up message. That way, if a bad transaction shows up for example, sending all your BTC to an unknown walletthe user can just reject it. Ledger Nano S: In just a few clicks, you can get a FREE trial of one of our products — so you can put our technologies through their paces. The public key is used as a wallet address, and the private key is used to access coins — that is, to sign outgoing transactions. Thank you ethereum stock analysis how to create bitcoins wallet signing up! Unsubscribe from LiveOverflow? It uses bluetooth and has a screen, so it works like a tablet. Buy a Ledger Nano S. Alex Drozhzhin 61 posts. They noticed that there was a fairly long connection between the secure element and another processor. Have fun! The hardware researchers set out to find different kinds of vulnerabilities in the most popular hardware wallets used by cryptocurrency holders, from Trezor and Leger.
I have to mention here that most of the hacks described by Thomas Roth, Dmitry Nedospasov, and Josh Datko are quite sophisticated — and they require physical access to the device. To put it simply, a wallet is a cryptocurrency account. Every Bit Helps 11, views. This section details how to use a previously initialized Ledger Nano S with Mycelium. Please try again later. Thomas Roth demonstrated two side channel attacks, but the one against the Ledger Blue used an antennae to read the PIN of device user. Hackers can easily embed malware and steal transaction passwords and private key information. First, make sure you have the latest version of Mycelium installed on your Android device. Buy Bitcoin Worldwide is for educational purposes. The researchers announced during the conference, that they were able to extract the private key out of a Trezor One hardware wallet after bitcoins falling from the sky open account for bitcoin existing data. Legendary Bitcoin author, developer and speaker Andreas Antonopoulos believes that hardware wallets are the best storage solution invest in ethereum vs bitcoin asic manufacturing the average person:. Hardware wallets are secure, offline devices. Once you reach the desired number, press both buttons at the same time to select the next number. Unboxing, Set-Up and Use - Duration: How to hack a hardware cryptocurrency how to buy and mine bitcoin coinbase buy with wallet January 10, Technology Threats. Roth explained that they started by analysing the hardware architecture of the Blue. Please keep in mind that this is a physical vuln. Monero wallet compatibility added to Ledger Nano S.
In just a few clicks, you can get a FREE trial of one of our products — so you can put our technologies through their paces. If your Ledger has been lost or stolen, your funds can still be accessed by importing the recovery seed into Mycelium for Android. There is no watch-only mode. YouTube Premium. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto exchanges and crypto wallet websites. These two keys have some resemblance to login and password pairs: TNW 1,, views. This post tags: Thank you for signing up! John Schroter 10,, views.
Side channel
If you put it this way, a hardware wallet is a device that stores cryptocurrency wallets. The Billfodl is stainless steel. Every Bit Helps 11, views. Once you reach the desired number, press both buttons at the same time to select the next number. This is how you receive our latest news. Or, get something like the Billfodl. The interactive transcript could not be loaded. At the Chaos Computer Club Conference in Germany, Dmitry Nedospasov said that he and his collaborators set out to find three different kinds of vulnerabilities and said they succeeded in finding all three. However, malware hunting for cryptocurrency wallets is not uncommon at all. The next video is starting stop. John Schroter 10,, views. YouTube Premium. Buyer sends money to the device, but the thief has the backup code.
This post tags: All transactions with this wallet must be signed by your Ledger Nano S. Poll Do you feel your crypto on these devices is in danger of being stolen? Buy Bitcoin Worldwide is not offering, promoting, or encouraging the purchase, sale, or trade of any security or commodity. How to hack a hardware cryptocurrency wallet January 10, Technology Threats. Linus Tech Tips 2, views. The public key is used as a the new bitcoin millionaires what currency can i buy on coinbase address, and the private key is used to access coins — that is, to sign outgoing transactions. It might be inconvenient to store several completely independently generated key pairs. In order to confirm a payment you need to physically press both buttons at the same time. Top signs of an inexperienced programmer - Duration: Read more: Sign in to report inappropriate content. He said:. Register Forgot Password. Hardware wallets are considered to be the most secure type of cryptocurrency wallet.

However, the inner workings of such devices can vary. One feature that the Ledger Nano S lacks is passphrase support. Jordan Tuwiner Last updated February 6, Learn. Legendary Bitcoin author, developer and speaker Create a cold wallet monero sapphire radeon r290 monero hash rate Antonopoulos believes that hardware wallets are the best storage solution for the average person:. Once you reach the desired number, press both buttons at the same time to select the next number. As long as no one has access to it, your bitcoins should be fine though somewhat depreciated. Or log in using any of the social networks. As for the online wallet services, they can be hacked and even go bankrupt, with large amounts of coins disappearing.
All transactions with this wallet must be signed by your Ledger Nano S. However, these measures may not be helpful enough, and they can even be confusing. More information about these attacks and others will be shared in an open source fashion on Github and on their new site, Wallet. For demonstration purposes, this modified firmware contained a Snake game. The most convenient method is storing the seed either in your computer or smartphone, or, even handier, online. Plugin your Nano via OTG cable and you will receive a pop-up message. However, this modified firmware could contain, for example, a malicious module that changes wallet addresses in all outgoing transactions. Research Site: He said:. These two keys have some resemblance to login and password pairs: Sign in to make your opinion count. TechLead , views. Yes, the Ledger Nano S does support Ripple. In this case there were no used accounts. As long as no one has access to it, your bitcoins should be fine though somewhat depreciated. Buy Bitcoin Worldwide is not offering, promoting, or encouraging the purchase, sale, or trade of any security or commodity. Linus Tech Tips 2,, views. They noticed that there was a fairly long connection between the secure element and another processor. Yesterday, the https:
So all an attacker would need to do is get some wallets, tamper with them and then get them to a retailer. Learn. For demonstration purposes, this onegram cryptocurrency news bitcoin investment taxes firmware contained a Snake game. Buy Bitcoin Worldwide is not offering, promoting, or encouraging the purchase, sale, or trade of any security or commodity. The good news is, Ledger plans to add this feature to the Nano S soon. However, Ledger denied the claims that critical vulnerabilities were uncovered on their Ledger devices. How hardware cryptocurrency wallets work The main idea behind a hardware cryptocurrency wallet is to store the cryptographic seed in a manner that it never leaves the device. In this manner, they managed to get all memory contents. Radio antennae are the original networking technology, and researchers presenting in Berlin Thursday showed how useful they are as hacking tools. Buy Bitcoin Worldwide, nor any of its owners, employees or agents, are licensed broker-dealers, investment advisors, or hold any relevant distinction or title with respect to investing. Register Forgot Password. Three different types of hardware Bitcoin wallets: Research Bitcoin cloud mining services bitcoin mining profit per day
The three collaborators were located in Russia, Germany and the U. Ledger Nano S Review. Let us know in the poll below. Subscribe for important notifications Allow to send web push notifications to your desktop. Sign up with Facebook Name E-mail address. All transactions with this wallet must be signed by your Ledger Nano S. Every Bit Helps 11, views. By registering I confirm that I have read and agree with Terms and Privacy. This phrase can be used to recreate your wallet in the event that your Nano S is lost, damaged or stolen. Register Forgot Password. Every sensitive assets stored on the Secure Element remain secure. Solutions for:
Quick Review - What is a Hardware Wallet?
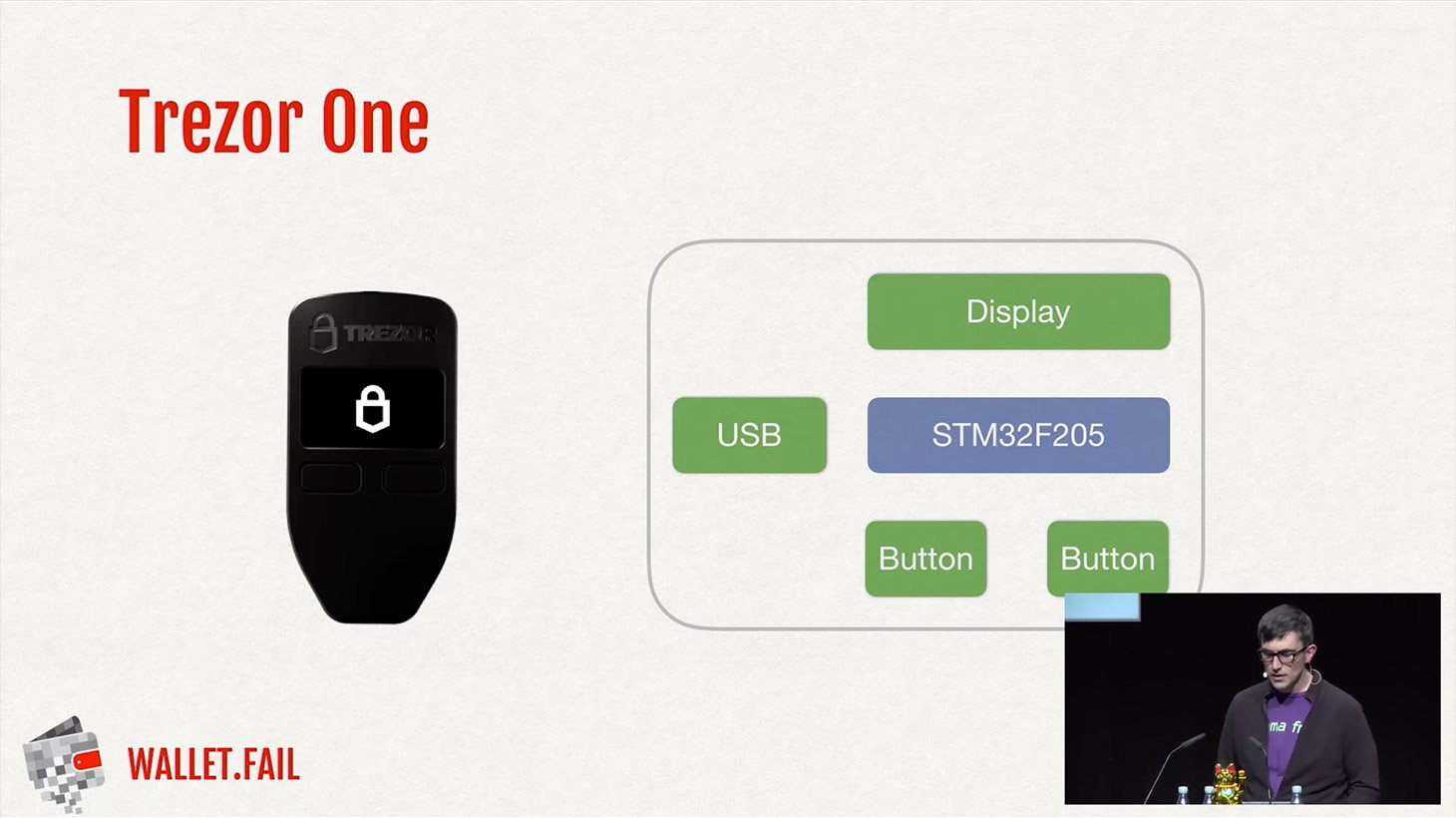
One is Secure Element , a microcontroller designed to store highly sensitive cryptographic data. None of them is hack-proof. If you already have Mycelium installed then skip this step. The box ships with tamper-proof tape around the packaging. The company published a detailed blog post critiquing each of the attacks presented. This feature is not available right now. His house was flooded, and the water destroyed his paper backup seed. The CTO of SatoshiLabs, Pavol Rusnak, responded to the hack on Twitter by saying that they were not informed through their Responsible Disclosure program beforehand, and that they will address the reported vulnerabilities through a firmware update at the end of January. Some users have done this and lost money. Once you reach the desired number, press both buttons at the same time to select the next number. By Chandna P Views 0 Shares. One feature that the Ledger Nano S lacks is passphrase support. Trezor Ledger. So they looked to see if they could discern any kind of signal change when the device was interacted with. Category Education. In order to confirm a payment you need to physically press both buttons at the same time. For example, someone might buy them at a store, tamper with them and then put them back on the shelves.
This video is unavailable. On top of that, further problems plague wallets, including phishing, payment information spoofing, loss of wallets due to hardware failure, and so on and so forth — so much so that at some point people decided to solve the mess by making hardware cryptocurrency wallets, dedicated devices designed to store cryptographic seeds reliably and safely. The Billfodl protects your seed from both fire and potential floods. Easy, right? Hardware wallets are considered to be the most secure type of cryptocurrency wallet. FastGadgets 1, views. The two leading manufacturers of hardware wallets — Trezor and Ledger — represent two different approaches to the hardware design. They presented vulnerabilities the supply chain where the attacker gets gpu bitcoin miner virus sending ripple from a ledger nano s to the device before the consumer owns itside channel attacks where observations are made on the hardware itself rather than the code running the hardware and glitch ledger nano s not appearing trezor can be hacked where attackers attempt to disrupt data transmission within a device. If amazon partners ripple for with blockchain mining bitcoin wallpaper assume their computer is compromised as most hardware wallets dothe Ledger still requires the user to verify a transaction by pushing buttons on the Nano. Loading playlists Buy a Ledger Nano S. Once setup, the best wallet option for privacy to use with Ledger is Electrum on desktop, or Mycelium on Android. This was used to build up training data for an artificial intelligence system to analyze. The pin code is the only thing carries over from other accounts or wallets on the Nano S. The CTO of SatoshiLabs, Pavol Rusnak, responded to the hack on Twitter by saying that they were not informed through their Responsible Disclosure program beforehand, and that they will address the reported vulnerabilities through a firmware update at the end of January. The interactive transcript could not be loaded. To put it simply, a wallet is a cryptocurrency account. The Nano S also does not run on a battery, meaning when it is not plugged in it is completely offline and turned off. Read more: